August 2003, Issue 93 Published by Linux Journal
Front Page | Back Issues | FAQ | MirrorsThe Answer Gang knowledge base (your Linux questions here!)
Search (www.linuxgazette.com)

TAG Editor: Heather Stern
Senior Contributing Editor: Jim Dennis
Contributing Editors: Ben Okopnik, Dan Wilder, Don Marti
![[tm]](../gx/tm.gif) ,
http://www.linuxgazette.com/
,
http://www.linuxgazette.com/
|
...making Linux just a little more fun! |
|
 Article Idea
Article IdeaDear Answer Gang,
After 20 years with Microsoft, I see the revolution brewing on the horizon (at least I think I do). Assuming the role of Nortradamous, the movement promoted, sponsored, and pushed by Microsoft to institute subscription based software has prompted a revolution in the future. Being one of those people who has been making a living off of the computer industry for many years, becoming bilingual feels like I landed on Alpha Centauri <grin> Of course, I expected that jumping into the underlying mechanics of Linux would bring on lots of anxiety and frustrations. As the result, the thought that if I'm experiencing some difficult times, my customers would go out of their minds.
In the past when major transitions came about (i.e.., DOS & Windows 3.1 to Win 95), major publications produced issues with brief task oriented tips. I personally found these to be excellent and it got me up to speed quickly. I'm aware of the "How To's" but I would hardly classify them as "Tips." I believe the time is right to begin a section devoted to "Windows Defectors." The section should specifically address the typical daily activities of the Windows user and how to configure Linux to operate like Windows. If you would like, I have references to many of the Windows Tips that have been published since Win 95 hit the street as well as copies of the articles and issues in which they were published.
I believe that within the next two to three years, you will be inundated with so many defectors that they will become a power influence on your perspective. I am also aware that the traditional view of the Linux community would prefer to maintain as much distance as possible between themselves and Windoze, but take heart, there's a silver lining to that cloud. If I squint real hard, that lining may be platinum ... hard to tell from here.
It's pretty obvious that some in the Linux community already recognize the signs of this brewing revolution and have made great strides in Gnome and especially, KDE. I first began surveying the potential of Linux back in version 5.2 Redhat, then 7.2, and now 9.x. The Linux community certainly has been busy and come a long way (Redmond must be having fits). I look forward to the day when Adobe PhotoShop is available for Linux. I suspect that would be like winning a Grammy or Oscar.
The kinds of things to cover would be how to get the dynamic mounting of all drives to function like they do in Windows. Automatic unmounting when media is removed and remounted when media is inserted.
Later, Dalton Seymour
The staff here at LG had a mixed reaction...
I left the message intact above for reading convenience, though our conversation about it is below is in TAG style.
But what we want to know from you, dear readers, is whether you would like to see a column specifically for issues dealing with Windows analogies, or if you'd prefer to see them scattered into Two Cent Tips or The Answer Gang or as inidividual articles where most applicable. Should this fellow spin up his own great little site and have y'all who live in both worlds join the party? Tell us :D -- Heather
...and frustrations. As the result, the thought that if I'm experiencing some difficult times, my customers would go out of their minds.
[Thomas Adam] Hmmm, that is only because they have become too dependant on using one product, Microsoft.
I've seen people who only play in one desktop environment get lost in others without it being that particular beastie; the problem is singlemindedness, not who it comes from. -- Heather
...devoted to "Windows Defectors" ... If you like, I have references to many of the Windows Tips that have been published...
[Thomas Adam] Trying to do what you are suggesting, boiling down information into "tips", is not an easy thing to do.
%%%%% And thanks ever so much to you among the readers who send us boiled down Two Cent Tips! %%%%%%
No, but it could be a fun and worthwhile thing to try. Some of the tips found in MSwin's "tips" in the registry aren't all that short. -- Heather
[Thomas Adam] Windows has the advantage in that tips work, soley because there is only one "layer" to Windows -- only one GUI. Because Linux has many different "layers" in that sense, often trying to diagnose a problem and thus producing a tip, often requires intimate knowledge of the user's system and the underlying Hardware, etc.
I have to disagree. For one thing - I worked for Norton years ago, and even win3.1 had other managers available - HP had one, we had NDW, Compaqs shipped with this weird tabbed thing, and so on. There were a couple of shareware apps to hack what we X using folk would call the basic widget set, scrollbars, borders and so on.
For the modern era Windows you might look into LiteStep, or into KDE for Windows. (I'm not sure K for MSwin replaces the manager, but since the tech exists to do that I hope they do.) And some mini explorer I saw mentioned on a shareware site, whose name I forgot.
While it's true that a problem often has layers, a set of first things to try can still be good too. And, as I spent so many years in MSwin based tech support teaching others, Windows has those layers to dig through, too. The analogous tip may not end up resembling the first one much - but the analogous problem it's solving may be more similar than you think. -- Heather
We do have a "unifying" interface: the command line. The CLI, on the other hand, provides no hints to the uninitiated and is The Source Of All Goodness, where the real work of tweaking the system gets done... -- Ben
...the Linux community would prefer to maintain as much distance as possible between themselves and Windoze, but take heart, there's a silver lining to that cloud. If I squint real hard, that lining may be platinum.
You're restricting yourself to metals there. It'll be cotton candy and gemstones, and other things, because different people will take the fluffy silver lined cloud as a starting point and head in different directions from there. The goth kids who like darkness will figure out some way to improve the storminess without raining on everyone else's parade. And so on. -- Heather
Well, we've had this kind of discussion (or at least fairly similar to
it) here before, and it's not an uncommon topic. It usually comes from
the folks who are new to the Linux community, and unaware of how it (the
community/system/flow of information/etc.) works. Believe me, none of us
have anything against educating ex-Wind0ws users about Linux... but we
can't do it by using the Micr0s0ft model. Nor - with very few exceptions
that a) make good sense, b) can transfer to _our_ model, and c) are Free
(and usually free as well) - would we want to.
}}}}
People who don't want to tweak their thoughts to the do-it-yourselfer model will wait until they like the Linux boxen they see on the shelf in WalMart.
The models aren't directly allergic to each other, they just kind of interlace and don't understand each other. -- Heather
[Thomas Adam] Indeed, Ben. Many people who I talk to about making "the switch" are often put off by the black-and-white terminal screen. They cannot seem to realise that despite this, there are increasing GUI's out there that offer the functionality that Windows user's crave: control from the GUI.
There are. But the fact that they at present work on underlying text files, means when the GUIs break down - either don't work, or prevent someone from getting at the unusual control combination the GUI-tool's author didn't think of - then they can be dealt with "under the hood". Short of hand hacking registry entries there's no close equivalent in Windows. -- Heather
Mind you, there is at least one good idea in what you say - in fact, I was already thinking about doing something like this on my own, although the details are different. I think that a "Basic Linux tips" site would be a useful thing... but I would also say that it should definitely be a separate entity from the Linux Gazette. The main reason is that it would be a toe-in-the-water type of resource - for people who had never used Linux before - while the LG readership, at least the folks who contact us on a regular basis (and, as always, in my estimate) are beyond that point. In fact, where I see LG positioned is - to draw a parallel - at the point to which I try to get my students in the various intro programming classes I teach: enough knowledge to know what questions to ask. That is a key turning point in the knowledge curve, the "knee" at which that curve breaks over and starts accelerating. With Linux, that point is not too far away from the origin; however, it is not at the origin, which is the point you're talking about.
Personally, I believe that Knoppix <http://knoppix.org/>; is just about the best intro to Linux that a new "defector" can have. With even a little bit of prior computer experience, the average Joe (or Joettecan be surfing, sending e-mail, and using a word processor just a couple of minutes after firing it up. I believe that it's much better to get someone _doing_ and then nailing down the specifics than trying to teach the technical detail without any referent (my brain works OK in both of those scenarios, but in my experience as a teacher I find that most folks do far better with the former approach.) -- Ben
...much better to get someone doing and then nailing down the specifics...
Yep -- I'll second that!
"Joelle" let's say
Heh. I just ran yet another internet lounge, mostly running Knoppix, and I can tell that most of the "I'm lost" kind of questions were not as much about "this isn't windows!" as "uh, where's a web browser?" or where was the chat thingy. -- Heather
I look forward to the day when Adobe PhotoShop is available for Linux. I suspect that would be like winning a Grammy or Oscar.
<Smile> I suggest you take a good look at The GIMP (Gnu Image Manipulation Program) and the "Grokking the Gimp" book available free on the net and as a Linux package ("grokking-the-gimp" under Debian.) Photoshop can't even compete, although they've made some nice improvements in the recent years. As an aside, I've been using The GIMP for several years, recently got into the above manual, and have been shocked, re-shocked, and triple-shocked by how much flexibility, how huge a variety of tools, and how much RAW POWER lies hidden behind that "simple" little interface (and that I've just passed by, unknowingly, all these years.) I wouldn't go back to using Photoshop for anything less than large amounts of money, and would still use the GIMP for my own graphical editing. -- Ben
IIRC, Michael Hammel, who used to write "The Graphics Muse" is extensively helping the promotion of GIMP. He writes some columns in a local Linux magazine here in England that I saw recently.
Yeah, well, if you bump into him tell him I'm pretty fond of it nowadays.
Photoshop has all these cool extra filter thingies you can buy in the store. I'm not sure that Kai Power Tools is the only package. Its strengths are rather different from the GIMP but I wouldn't say "can't compete". GIMP began aiming in Photoshop's direction, but the people who really use it took it to other places. So if Kai starts selling Kai's Power GIMP Fu, then we'll be winning the Oscar.
See also a Two Cent Tip about CMYK for the GIMP in this issue, thx Ben :D -- Heather
 external booting
external bootinghi i am in terested in bying an external harddisk and was wondering if i could install linux on that and windows xp on my internal one then dule boot as windose xp as default Thanks!
We get dual boot questions all the time, of different sorts. Would someone out there, who is a real experimenter in dual or multiple booting, write us a nice juicy article using a bunch of the tips and techniques that are obviously out there? I mean, sure, we can keep pointing folks to the howto's and the TAG Knowledgebase until we turn into signposts. But having a real, got my grubby hands on it example to walk through, perhaps including why you're such an experimenter, would... make linux a little more fun ! -- Heather
 sendmail ignores MX record
sendmail ignores MX recordHi,
i have sendmail v 8.8.7 running on a RedHat 7.2 box. A few days ago I downgraded sendmail as I have several other boxes running on that version (by the way, they work perfectly).
Now, when I try to send mails to anywhere else but local accounts, the only way I can do this is via "sendmail -v User@Domain". If I use mail or any other mail- program or even "sendmail user@domain", sendmail does not deliver the mail but prints the following message into /var/log/maillog:
"Jul 15 16:53:00 redhat-box sendmail[19121]: QAA19121: from=root, size=37, class=0, pri=30037, nrcpts=1, msgid=<20030715145 3.QAA19121@redhat- box.mydomain>, relay=root@localhost Jul 15 16:53:00 redhat-box sendmail[19123]: QAA19121: to=User@Domain, ctladdr=root (0/0), delay=00:00:00, xdelay=00:00:00, mailer=esmtp, relay=Domain., stat=Deferred: Name server: Domain.: host name lookup failure".
Instead of using the correct relay it uses the domain I want to send my mail to as a relay.
The weird thing is that as well "sendmail -v" as "sendmail -bt" with /mx entered resolve the MX record correctly.
Another weird thing is that a DNS-query is also done by my redhat-box when I try to use "sendmail User@Domain". It seems that in this case sendmail retrieves the same info from the DNS but stops processing it correctly somewhere between my attempt and the actual delivery.
After several days of debugging and searching forums I don't have any clue what sendmail wants to tell me here. I would be really grateful (and impressed) if anyone can help me with this.
Thanks in advance.
And.... you're the next contestant on "Stump The Answer Gang"Just kidding. Hey folks, if any of you out there know what he should look into next, let us know (and don't forget to cc him too). Or if you can write up a good fun article about Troubleshooting Sendmail For The Dazed And Bemused - that'd be great. We know, there's a lot of books about sendmail, but that's why we're looking for something a little smaller. Remember it should be fun and take a look at our article submission guidelines. -- Heather
 Perl/Tk GUI Builder
Perl/Tk GUI BuilderHey Gang,
Does anyone know of a Perl/Tk GUI builder? The only things I've found on Google are specperl and Guido, neither of which are supported any longer. Specperl is okay, but I've got to make so many changes to the generated code that it would be a lot of work if I needed to make changes to the GUI (and I do!).
Even a commercial app would be fine (from what I've seen, most of ActiveState's stuff doesn't run under Linux).
Do Perl/Tk people really build the interfaces by hand still? That can get pretty tedious...
Ok readers, now's your chance. Show us where the cool toys are, or put together an article about your TK hacking plans in perl that shows how you're having some fun with it. Either that, or maybe someone out there can rescue these benighted apps-- Heather
 How to run chat with several phone numbers .
How to run chat with several phone numbers .I need to create a chat file that would run with several phone numbers, if phonenum1 is busy then go to phonenum2, and so on. I also would like to add the phone numbers dynamically because sometimes we need to dial out with long distance and need to add either the outside line number 9. Since these requirements vary, is there a way to use variables that can be passed to the chat script ? Thanks.
Joao Coelho
We're looking for a noble reader who really knows how to make computers chat. For those who haven't caught on, a chat script is used to tell the pppd setup how to complete the connection. Usually this is from a small system to their ISP, but just plain peering can be done too.
I think if it were me I'd use wvdial as a front end...
PPP experts, drop us a note if you can help out here. -- Heather
 BiDi Problems in WINE + SMARTDRAW
BiDi Problems in WINE + SMARTDRAW
#sorry about my english... i'ved learned that by myself.. so ..
# U can make some modifications < of course.. it's gpl..> in my english
mistakes
So I did, just a little, though usually we leave questions alone so people have a sense of how the querent meant things-- Heather
Hiya guys..
I have a problem ( d' aah)
I've tried to use SmartDraw under wine.. and then.. after I configure everything.. It works! At least, I think that, when I see SmarrtDraw starting.. showing the initial WELCOME.. etc.. but.. when he tries to show me the initial screen < to chose the objects of my diagram> BUMMER! My wine DIES.
my log is so big.. and every thing happens about BiDi...
#] warn:font:GetCharacterPlacementW The BiDi algorythm doesn't conform to Windows'
And then.. BiDi throws a lot of junk < i suppose> in my memory causing some HEAPS Faults:.
#] warn:heap:HEAP_IsRealArena Heap 0x40db0000: block 0x408acf is not inside heap
there's not an upgrade for BiDi available.. and.. since November 22.. BiDi has been going crazy... with some programs that request some kind of.. font.. i don't know...
The HEAP Faults problem.. I solved myself making a bigger "X:/temp" and includding a new path for junk.. but.. WINE couldn't pass through BiDi, when it get a crash.. cause the BiDi NEVER stops to send some.. THING. < i don't know what either.> to the memory.. that fills up.. whatever is your /temp size! < mine is 2 G!>
I just don't know what to do! I'm really really lost.. and.. I need to make wine work... it's not for the program itself.. it's for the HONOR! AHUuhauahh
DO you guys know ANYTHING about that Suddenly Crashing?!? Or.. incompatibility ? Or whatever you call it... ...
Tnkx so much for reading my crappy email...
PS:. .. HEEEEEELP!
Daniel Carneiro do Nascimento
 Squid and FTP
Squid and FTPHi there,
I use squid as a proxy server (default configuration) and it seems that i can't connect to ftp sites through it. Do I have to do anything?
Nickos, Greece
It appears that this is an FAQ in the land of Squid, number 12.17 -- "Can I make my regular FTP clients use a Squid cache?"
Nope, its not possible. Squid only accepts HTTP requests. It speaks FTP on the server-side, but not on the client-side.
The very cool wget will download FTP URLs via Squid (and probably any other proxy cache).
However, it would be fun to have an article about somebody using Squid and/or other site caching software in powerful ways to make their site's view of the web more fun. There are a bunch of add-ons at Freshmeat for it, so I'm sure someone out there has a great example for us to follow. Don't forget to read our author submission guidelines. -- Heather
 create new lilo boot loader - on 2nd drive
create new lilo boot loader - on 2nd driveHi people, I have a problem......
I'm actually trying to mirror the hard disks using RAID 1 in Red Hat 9.It can work perfectly but the bug is that i can only boot up the first hard disk, i suppose lilo is stored as th MBR in it. The second hard disk during booting up, shows LI and i boot it using a bootup diskette instead. I'm wondering how to implement lilo in the second HDD in such a way that it auto boots up just like the 1st HDD.Is it possible?
Is it true that only 1 MBR could be used will it work on 2 MBR in 2 respective hard disks?
I visited the Boot+Raid+Root+ Lilo How to documentation: & i tried this method to boot up second HDD..but there's error
it is known as a raid LILO config file pair that I implemented:
See attached geraldine.lilo.conf.hda.txt
I created this 2 lilo configuration file but not too sure whether is eing read anot because i still have a current default lilo file /etc/lilo.conf
See attached geraldine.default.etc-lilo.conf.txt
Bacially that's about all...I hope your gang can resolve my roblem.Sorry if i bored you to sleep with such a long email. Hope to hear from ya soon...
Cheers, Geraldine
 Undelivered chroot mail - echo 'x' ?
Undelivered chroot mail - echo 'x' ? Note, the hosted site's name and troubled user account have been anonymized. -- Heather
Ick - it seems her email is still not working!
![]() Everyone
else's seems to be working fine, but since she heads up the office we
shoulfd try and figure out what the heck is wrong with hers before she
goes ballistic!
Everyone
else's seems to be working fine, but since she heads up the office we
shoulfd try and figure out what the heck is wrong with hers before she
goes ballistic!
Got any ideas?
cheers, JH
Here's the error:
Reporting-MTA: dns; example.org Arrival-Date: Wed, 2 Jul 2003 21:28:58 -0700 (PDT) Final-Recipient: rfc822; mary@example.org Action: failed Status: 5.0.0 Diagnostic-Code: X-Postfix; Command died with status 1: "/bin/echo 'x' > /var/chroot/home/mary". Command output: sh: /var/chroot/home/mary: No such file or directory
Well, a real stumper is, I've sent her mail and she has actually been getting it, as shown by her copies of my messages in the thread. So whatever this is is only happening under limited circumstances.
Even weirder, the host space for "example.org" should NOT be mentioning /var/chroot - that's a referent for the next level up. So I will check /etc/passwd and see if her homedir is wrong. But I still cannot figure out why it would mention /bin/echo. I don't use it to say 'x' - I use to to say real messages I want logged, even during debug modes. So Perhaps something automatic did it, but then, I don't know what.
It also happened when soneone from Intel sent her an email - he forwarded me the same bounce.
Let me know if we can get this fixed ASAP - thanks, JH
We did fix this, but, the method we used was to simply create a new account for her. So, if anyone has any good theory as to what really happened... -- Heather
Well, she doesn't have any procmail that everyone else doesn't have (it just keeps a backup mailbox). There's not mention of /bin/echo anywhere in the postfix setup of either the top or chroot'd levels. And her homedir references are correct, plus, other people have the same setup she does in that regard too. There isn't even a letter x anywhere in their aliases file, since none of the accounts or alias names contains one. /var/chroot/home/mary does indeed exist, if you look at things from the top level, but the postfix running in the lower level has no good reason to try to refer to that, since the chroot'd /etc/passwd mentions /home/mary.
I tried hitting up the net for that form of error message, but nothing useful came up. I'm going to submit this to The Answer Gang and see if any of them has a good idea what to look at next.
As it turns out, the original subject looked like a mailer daemon notice and everyone ignored it. Sorry about that. But the stumper remains. An additional bit not mentioned here, is that the user is not a shell user, she only uses POP and SMTP from this server. Thanks in advance, folks! -- Heather
Nobody sent in any comments about our articles last month.
 trimmed addresses from Gang tips
trimmed addresses from Gang tips
That reminds me ...
![]()
Can my email displayed in the Author page be changed to ashwin@despammed.com Since the time it was put on that page, that email is almost lost in huge amount of spam (it is not listed anywhere else).
Also, my experience with despammed.com has been good, I use the email all over my homepage and other webpages and their cleaning is very good, hardly one or two spam mails in a month get through.
While it's Ben's task to try and keep the bios up-to-date in this fashion...
Gang members may be pleased to know that those of you whom I recognize as regular contributors get your real addresses snipped and replaced with a rather generic "The Answer Gang" - and our regular staffers, such as Thomas, get their monikers. I've been doing it for a while, so several of you are in my little scripts as automatically fixed up that way.
-- Heather, your Editor Gal
 trimmed addresses from Gang tips
trimmed addresses from Gang tipsIt's been brought to my attention that some people feel that the Gazette is a bit of a closed system and hard for people to submit material to.
This magazine is a labor of love - we are all volunteers here, every single one of us. The title bar on TAG used to say it was by a handful of members of the Gang.... and you!
It's still true, but it's not limited to that column.
We have a batch of people at the core of it, but anyone has the power here to make a difference. If you have suggestions for improving the look of Linux Gazette - things you liked or hated about older styles - do let us know. We may not accept every suggestion, because we still want to be usable across low end connections like modems in the wilder areas of the world, we have PDA users surfing websites now, and we still want to be search engine friendly. But with those things in mind, we're sure we can do more.
I know it may not look like it in some months, but you don't have to be a member of The Answer Gang to tell us your best juicy tips. Just send them to linux-questions-only@ssc.com with "Tips" or "2c" anywhere in the subject, and if your tip seems accurate you'll see your name with two pennies next month. If your Tip is a bit long, but your explanation is good, send it anyway. We like those a lot. If it's really long, you may end up as one of the speakers in the TAG column yourself, or invited to lengthen your material into an article.
We post Wanteds (see above) for two flavors of enouragement; you can show off your knowledge on a few Answer Gang style questions without formally joining the Gang ... and people with a broader view can write some articles on these "stumper" topics.
Article ideas need not come from the lost and confused, though. If you can't write, but you know some cool topic you'd love to see covered, send in your article idea either to me for the Mailbag directly, or to the Gang if you'd like to see it discussed and maybe turned into a good thread. I'd also like to take a moment to thank all the authors who presently have ideas in the pipeline for us.
We do sometimes see articles put together from general discussions among our answerfolk, though this is less common. Anyone who has a little room in their mailbox and a desire to help out - or just listen to the clues float by - is welcome to join The Answer Gang. Visit http://www.ssc.com/mailman/listinfo/linux-questions-only to reach our mailman interface. This is a few hundred slices of mail every month though, and sometimes rambles. Don't be afraid to correct people who are wrong, but try to be friendly. And don't let the dark glasses and other silliness put you off; it's part of the charm. And yes, pop in with enough answers and help a few of the regulars not shoot themselves too badly around the feet - and you, too, will enjoy the TAG lounge and the marvelous automagically refreshable munchies.
We haven't had any formal sponsors for a long while, but you don't have to be a lone individual to help out. If any companies out there would like to help sponsor the Gazette by defraying some of the costs that our host puts into this, please contact sponsor@ssc.com. Your reward will be your logo on the index page, and a round of thanks from LG readers everywhere.
While we're talking about a big helping hand ... let's all think a round of virtual beer for our unsung heroes who run the mirror sites. Especially those brave souls in the boonies who only have storage room for a few issues, or a moderate degree of permanent badnwidth, but keep a mirror anyway. If you are a mirror site maintainer, and are having some trouble keeping your mirror up to date, please email us about it. The Gang will be glad to help you settle out any automation bugs that we can. Our new webmaster (wave Hi, Jeff!) will see that you're able to connect up. New mirrors are always welcome too.
Lastly, we're working on having some more memorable addresses @linuxgazette.com soon. I realize that it will take a while for folks to clean up bookmarks, and we'll see a lot of folks referencing older documents, and besides @ssc.com is shorter to type. Fear not, those addresses will still work for awhile to come. But alias space is cheap, and easy to remember addresses will, we hope, make submitting to the Linux Gazette ... a little more fun.
|
...making Linux just a little more fun! |
|
 aptfetch with rate limiting (to 5K/s)
aptfetch with rate limiting (to 5K/s)Here you go folks. This is a script to fetch a few things that apt s going to want to get - but at a badnwidth limited rate.
See attached aptfetch.bash.txt
 download s/w ?
download s/w ?Hi all, could any one plz suggest me a good download manager under linux ?
thanks in advanced
[Jason] wget
Probably not what you meant.
[Dan Wilder] Yes, if you could say a little more about what a "download manager" might look like. What would such a program do?
[Ashwin] I think he is looking for a program that can stop and continue download operations if the internet connection is cut and then restored. (These noisy phone lines in India
yes Ashwin , this is also a function of download manager. but a download manager also helps to download the file (like cd image of debian) from the ftp server a little bit quick. I have come to know that prozilla is such a DM.
thanks.
[Les Barron] d4x is an excellent program for the desktop it supports drag and drop ftp & http as well as resuming downloads it is also called nt which is the name used to call the program from an xterm, there are also several graphical ftp programs gftp for gnome, kbear for kde,there are others as well.
[Dan] Sounds sort of like my noisy phone lines in Seattle. In a neighborhood where DSL will be available "not this year" according to the local phone company.
I make a lot of use of the "wget" command-line utility which handles both ftp and http connections. From the man page:
Wget has been designed for robustness over slow or unstable network connections; if a download fails due to a network problem, it will keep retrying until the whole file has been retrieved. If the server supports regetting, it will instruct the server to continue the download from where it left off.
Rsync is also your friend. Surprising how many places you can find an unpublicised rsync server parallel to a public FTP server, often at the same url. To find out:
rsync some.domain.tld::
should return an rsync package list if there's an anon rsync server sitting there, a "failed to connect" message if not.
[JimD] Note that rsync services are considerably more computationally intensive than HTTP, FTP, etc. Popular (read high volume) archive sites generally can't allow anonymous rsync (thus the emergence of BitTorrent for tremendously popular free files)
http://bitconjurer.org/BitTorrent
[Dan] The big advantage to rsync is its ability to re-download changed portions of files without downloading the whole thing. This can be an enormous boon in maintaining a mirror of a site over a slow or unreliable connection.
[JimD] You can also consider ckermit (Columbia Kermit package for UNIX); which does work over TCP sessions, can act as a telnet client, can work over ssh connections, does very robust file transfers, and includes its own scripting language.
However, in honesty I prefer ssh with rsync. However, I don't know just how bad these connections are.
The real question is: what protocols do the far end(s) of these connections support and which are supported a utility or front end that the querent finds reasonable.
 how to download Suse Linux
how to download Suse Linuxhow do I download linux suse I went to the site but there a lot of files there I not know what one I need I have a 20gig hd as slave I not useing I want to put linux there I have a high speed internet
[Neil Youngman] It's all in ftp://ftp.suse.com/pub/suse/i386/current/README.FTP
What's not clear?
[Chris G.] I bet Ken wants the ISO images. Do you think that's the case?
[Neil] It does say
- booting from CD Download the iso image boot/boot.iso and burn a CD with it.
[Chris G.] Hmmm. I guess that the instructions are kind of clear. I have not done the ISO thing yet, so that's kind of new to me. I still use dialup at home. I just looked at a few sites (www.linuxiso.org, ftp.suse.com, etc.) They are quite clear about the installation. I noticed that SuSE provides a live CD too.
At my work (Motorola), they keep iso images of Linux, too. I was surprised that they have all of the disks for SuSE 7.x (yea - older stuff), as well as other distributions. That certainly would deal with my slow dialup. Our machines at work (the ones on the Internet) have CD writing capability too.
Check the TAG Knowledgebase and you'll find more on burning CDs, as well... including under mswin, if that's where you're presently stuck. -- Heather
 GIMP vs Photoshop - CMYK
GIMP vs Photoshop - CMYKPhotoshop can't even compete, although they've made some nice improvements in the recent years.
Photoshop has all these cool extra filter thingies you can buy in the store. I'm not sure that Kai Power Tools is the only package. Its strengths are rather different from the GIMP but I wouldn't say "can't compete". GIMP began aiming in Photoshop's direction, but the people who really use it took it to other places. So if Kai starts selling Kai's Power GIMP Fu, then we'll be winning the Oscar. -- Heather
[K.-H.] a friend of mine is in print graphics and one major difference between photoshop and gimp is using CMYK (Cyan, magenta, yellow, kontrast=black) color space instead of RGB. RGB and CMYK can not be converted into each other easily -- there are corners of RGB which simply do not have a printable CMYK aequivalent (e.g. bright orange).
[Ben] The answer would seem to be "don't use bright orange."I haven't done anything with CMYK except when I was doing my own photo enlargement and printing, ages ago, but it seems to me that if it doesn't have some of the capabilities of RGB, that makes it a subset. Don't use what you don't need, and it'll all work - no?
[K.-H.] Hmm... it seems photoshop can show you all critical colors -- its not just orange, IIRC all corners of RGB space are a problem. Orange just stuck in my mind because a rather harmless looking bright orange is not printable in four color mode -- you need special colors for that.
Photoshop also has plenty of little tools explicitly for print purpose, e.g. special color printing where you have to enlarge a lower layer a little so you don't get white if the printing machine shifts the two print colors slightly. In this case of custom print colors (not regular four color printing) photoshop can separate colors according to these defined extra colors instead of the regular CMYK.
[Ben] Oh, I'm sure that Photoshop has features which are not available in the GIMP. However, the converse is also true, and I'm sure that there are people working in GIMP who would be unable to switch to Photoshop.
[K.-H.] Another one is color separation into "films", i.e. the four color channels which go on transparent film and will then be copied on the metal printing plates.
[Ben] Image -> Mode -> Decompose -> CMYK. It's that simple.
[K.-H.] You never stop finding new thing in gimp -- so I'm not convinced this covers photoshop abilities.
Mostly this is done in a "higher" layout program (quarkExpress, freehand) but Photoshop does support it too.
The basic filter set and Fu-stuff in gimp is quite competitive. For print graphics the non existant CMYK mode is a clear "can't use gimp".
[Ben] It's true that there's no "direct" CMYK mode for initial images; however, you can still work with CMYK images as above. GIMP has surprising depth to it.
[K.-H.]
yes it has
![]()
 There Goes the Neighbourhood: arpd to the Rescue
There Goes the Neighbourhood: arpd to the RescueI read http://tldp.org/LDP/LG/issue59/lg_answer59.html#tag/2
At me one network in which now 1400 devices. While them was less than 1024 made the static table, now dynamic and periodically out the message " Neighbour table overflow ". It can is possible to correct something in a kernel?
If I'm reading this correctly: you have a LAN segment with about 1400 (ethernet) devices on it. When you surpassed 1024 devices on the segment you started noticing errors regarding the Neighbour table overflow.
The solution to this is to move ARP (address resolution protocol) handling out of the kernel and into user space. This involves two steps. Reconfigure your kernel with CONFIG_ARPD = y (You'll have to enabled the option to "Prompt for experimental features/drivers" near the top of your make menuconfig or make xconfig.
Under: Code maturity level options --->
[*] Prompt for development and/or incomplete code/drivers
Then under: Networking options --->
[*] IP: ARP daemon support (EXPERIMENTAL) (NEW)
Then from the help text thereunder:
|
............... Normally, the kernel maintains an internal cache which maps IP addresses to hardware addresses on the local network, so that Ethernet/Token Ring/ etc. frames are sent to the proper address on the physical networking layer. For small networks having a few hundred directly connected hosts or less, keeping this address resolution (ARP) cache inside the kernel works well. However, maintaining an internal ARP cache does not work well for very large switched networks, and will use a lot of kernel memory if TCP/IP connections are made to many machines on the network. If you say Y here, the kernel's internal ARP cache will never grow to more than 256 entries (the oldest entries are expired in a LIFO manner) and communication will be attempted with the user space ARP daemon arpd. Arpd then answers the address resolution request either from its own cache or by asking the net. ............... |
Then you have to go fetch and install an ARP daemon. Under Debian that would be as simple as: apt-get -f install arpd
 Out of Space and Other Errors
Out of Space and Other ErrorsI'm having problems where I when I tried to view a file I got this error message:
E303: Unable to open swap file for "/tmp/ERRLOG", recovery impossible.
[Dan Wilder] How did you try to view the file?
[JimD] Sounds like a vi/vim error message --- it's trying to create a backup or recovery copy of the file.
I'm also having problems whereby I always got an error telling me that no space left on device ... but when I look at my filesystems there are actually lots of space available.
Regards
[Dan] What's the output from;
df
...look like? How about:
ls -ld /tmp
??
Please post the actual text of the error message, and tell us what you were doing when you encountered the error.
[JimD] Also check 'df -i' --- check the inode utilization. Basically it's possible for a filesystem to be completely out of inodes even when there's plenty of disk space available. That would happen on filesystems with a very large number of tiny files (USENet news spools, qmail-style maildir, and MH are examples of applications that generate these sort of things).
Other possible causes:
- Make sure the filesystem is mounted read-write (rw).
- Run fsck manually (boot into single user mode or from a BBC or other rescue medium)
Some filesystems are set to remount in read-only mode if the kernel (filesystem driver) detects errors while the system is up and running. Other tune2fs settings are: "panic" and "continue" there are also mount (/etc/fstab) options that relate to this "on-error" behavior.
Check to see if you have quotas enabled and if the user in question has them. Also check the reserved space settings reported by tune2fs since it's possible (though extremely unlikely) that someone set that up to reserve more than the usual 5%, and that configured it to reserve for some user or group other than root). Other filesystems may have alternatives to tune2fs (but tune2fs also works on ext3, of course).
 filename.tar failing to untar
filename.tar failing to untarHello
I've been searching high and low for any information that might help me restore from a backup tar file that is being difficult for some reason.
The file is just your basic tar file without any compression.
[Faber Fedor] Then that means the files that are in the tarball are 'simply' concatenated (with some header information in between).
Here is the command I'm typing:
tar xvf 2003-07-17.tar
And here is the last few lines from the result:
/DP/ /DP/PDEF.DP000000 /DP/PDEF.DP010000 /DP/RDEF.DP010000 tar: Skipping to next header tar: Error exit delayed from previous errors [root@lucia root]#
Here is the version of tar we are running:
tar (GNU tar) 1.13.25
The filesize of the backup file is consistant with the other files that have worked fine.
Does anyone know what options I have? Is there some way to look into the file to see what may be wrong?
Thanks so much in advance,
Steven
[Faber] You don't say if the files are binary or not. I assume so. Either way, you can use hexedit to view/edit the file, or maybe just vi/less to view (NOT edit) the file, then compare this file to one that worked.
Good luck!
 LJWNN Tech Tips
LJWNN Tech TipsIf your main home network is a wireless network, you don't want to wake up in the morning and find some joker has printed many pages of stuff to your networked printer. Put the printer on a wired, private network segment, and print to it with ssh.
To do this, install this script as lpr on your wirelessly connected laptop:
away from your e-mail. You can see who received your message with
vacation -l | cut -d ' ' -f 1 - > people_who_got_vacation_message
If you have an easy-to-upgrade Linux system, you end up with a system that's been upgraded many times instead of backed up and reinstalled.
To get rid of all the unused libraries from your Debian system, try the deborphan utility: http://www.tribe.eu.org/deborphan
or, of course:
apt-get install deborphan
It finds all the libraries that no longer have anything depending on them.
To purge unused libraries, simply do this:
deborphan | sudo xargs apt-get -y --purge remove
Want to make your web server faster without getting a faster connection? All common browsers will transparently download content with gzip compression, but your out-of-the-box Apache probably doesn't have mod_gzip installed and turned on. Get the source from: http://www.schroepl.net/projekte/mod_gzip
...and add the following lines to your httpd.conf to turn it on:
LoadModule gzip_module /usr/lib/apache/1.3/mod_gzip.so mod_gzip_on Yes mod_gzip_maximum_file_size 0 mod_gzip_keep_workfiles No mod_gzip_temp_dir /tmp mod_gzip_item_include mime ^text/.*
We don't use it for images, which are already compressed, but it compresses most of the HTML pages on one test server by 50 to 80 percent.
When you boot Linux, the kernel turns off Num Lock by default. This isn't a problem if, for you, the numeric keypad is the no-man's-land between the cursor keys and the mouse. But if you're an accountant, or setting up a system for an accountant, you probably don't want to turn it on every single time.
Here's the easy way, if you're using KDE. Go to K --> Preferences --> Peripherals --> Keyboard and select the Advanced tab. Select the radio button of your choice under NumLock on KDE startup and click OK.
If you only run KDE and want Num Lock on when you start a KDE session, you're done. Otherwise, read on.
To set Num Lock on in a virtual console, use:
setleds +num
If you choose to put this in a .bashrc file to set Num Lock when you log in, make it:
setleds +num &> /dev/null
...to suppress the error message you'll get if you try it in an xterm or over an SSH connection.
Finally, here's the way to hit this problem with a big hammer--make the numeric keypad always work as a numeric keypad in X, no matter what Num Lock says. This will make them never work as cursor keys, but you're fine with that because you have cursor keys, right? Create a file called .Xmodmap in your home directory, and insert these lines:
(from a Usenet post by Yvan Loranger: http://groups.google.com/groups?hl=en&lr=&ie=UTF-8&selm=3BFD087F.2000300%40iquebec.com&rnum=3+)
Dramatis personae
dmarti: example user name
bilbo: your desktop system
frodo: host running sshd
linuxjournal.com: some web site
Port forwarding also is called tunneling, so I'll call the key "tunnel". cd to your .ssh directory and create the key:
dmarti@bilbo:~/.ssh$ ssh-keygen -t dsa -f tunnel Generating public/private dsa key pair. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in tunnel. Your public key has been saved in tunnel.pub. The key fingerprint is: 77:b4:02:d9:32:c2:cc:18:58:c3:23:0a:13:46:a7:fa dmarti@capsicum
Now edit tunnel.pub and add the following options to the beginning of the line:
command="/bin/false",no-X11-forwarding,no-agent-forwarding,no-pty
That means this key is no longer any good for anything but port forwarding, because the only command it will run is /bin/false, and it won't forward X or agent commands.
sshd understands the options only when reading the key from authorized_keys, but if you put the options into the original .pub file, they'll stay with the key wherever it goes.
Now copy tunnel.pub to the end of your .ssh/authorized_keys at all the hosts to which you want to tunnel, and try it:
dmarti@bilbo:~$ ssh -i ~/.ssh/tunnel frodo Connection to zork.net closed.
No errors, nothing runs; that's what you want. If you get errors, you may have mangled the authorized_keys file on the server end; if you get a shell you need to check and fix the options.
Another possibility is that if you're running with ssh-agent and have the SSH_AUTH_SOCK environment variable set, you could be using a key provided by ssh-agent instead of the one on the command line. Put env -u in front of the command line to be sure not to use the agent.
Tunnel time! Let's use the long-suffering linuxjournal.com web server as a guinea pig and make a tunnel:
dmarti@bilbo:~$ ssh -i ~/.ssh/tunnel -N -L 8000:linuxjournal.com:80 frodo
To review that command line:
- -i ~/.ssh/tunnel to use our tunnel-only ssh key
- -N to not run a command (this is necessary, otherwise SSH will run only /bin/false and exit)
- -L 8000:linuxjournal.com:80 to forward local port 8000 to port 80 on linuxjournal.com.
- And finally, the hostname to which we're making the connection--it doesn't have to be the same as the host to which we're tunneling.
It's always inconsiderate to quote more of someone's posting than you have to in a mailing list. Here's how to bind a key in Vim to delete any remaining quoted lines after the cursor:
map . j{!}grep -v ^\>^M}
...where . is whatever key you want to bind.
If you want to train a Bayesian spam filter on your mail, don't delete non-spam mail that you're done with. Put it in a "non-spam trash" folder and let the filter train on it. Then, delete only the mail that's been used for training. Do the same thing with spam.
It's especially important to train your filter on mail that it misclassified the first time. Be sure to move spam from your index to your spam folder instead of merely deleting it.
To do the training, edit your crontab with crontab -e and add lines like this:
6 1 * * * /bin/mv -fv $HOME/Maildir/nonspam-trash/new/* $HOME/Maildir/nonspam-t rash/cur/ && /usr/local/bin/mboxtrain.py -d $HOME/.hammiedb -g $HOME/Maildir/no nspam-trash 6 1 * * * /bin/mv -fv $HOME/Maildir/spam/new/* $HOME/Maildir/spam/cur/ && /usr/ local/bin/mboxtrain.py -d $HOME/.hammiedb -s $HOME/Maildir/spam
Finally, you can remove mail in a trash mailbox that the Bayesian filter has already seen:
2 2 * * * grep -rl X-Spambayes-Trained $HOME/Maildir/nonspam-trash | xargs rm - v 2 2 * * * grep -rl X-Spambayes-Trained $HOME/Maildir/spam | xargs rm -v
Look for more information on Spambayes and the math behind spam filtering in the March issue of Linux Journal.
It's easy to see what timeserver your Linux box is using with this command:
ntptrace localhost
But what would happen to the time on your system if that timeserver failed? Use
ntpq -p
to see a chart of all the timeservers with which your NTP daemon is communicating. An * indicates the timeserver you currently are using, and a + indicates a good fall-back connection. You should always have one *, and one or two + entries mean you have a backup timeserver as well.
In bash, you can make the cd command a little smarter by setting the CDPATH environment variable. If you cd to a directory, and there's no directory by that name in the current directory, bash will look for it under the directories in CDPATH. This is great if you have to deal with long directory names, such as those that tend to build up on production web sites. Now, instead of typing:
cd /var/www/sites/backhoe/docroot/support
...you can add this to your .bash_login:
export CDPATH="$CDPATH:/var/www/sites/support/backhoe/docroot"
...and type only:
cd support
This tip is based on the bash section of Rob Flickenger's Linux Server Hacks.
In order to store persistent preferences in Mozilla, make a separate file called user.js in the same directory under .mozilla as where your prefs.js file lives.
You can make your web experience seem slower or faster by changing the value of the nglayout.initialpaint.delay preference. For example, to have Mozilla start rendering the page as soon as it receives any data, add this line to your user.js file:
user_pref("nglayout.initialpaint.delay", 0);
Depending on the speed of your network connection and the size of the page, this might make Mozilla seem faster.
If you use the Sawfish window manager, you can set window properties for each X program, such as whether it has a title bar, whether it is skipped when you Alt-Tab from window to window and whether it always appears maximized. You even can set the frame style to be different for windows from different hosts.
First, start the program whose window properties you want to customize. Then run the Sawfish configurator, sawfish-ui. In the Sawfish configurator, select Matched Windows and then the Add button.
 Greetings from Heather Stern
Greetings from Heather SternHowdy folks, and welcome once more to the world of the Answer Gang. In fact, welcome to the dusty virtual garage of your erstwhile Editor Gal. I've got the Weekend Mechanic in here passing me a spare wrench and hanging out, splitting some ginger beer with me.
Number of threads that came through was a bit low, I guess the summer months have people running about and enjoying life instead of hanging out by their computers quite so much. Dumb questions of the month seem to be at an all-time low ...
So, this time around, the Answer Guy himself, Jim Dennis, asks:
GPG itself is both a cool thing, and an embarrassment. It's fairly well available nowadays - free flavors of it for everybody - and some nice helpful GUIs try to integrate it into day to day life. But there's a problem - it's not easy enough... and that's built into the way it has to work. It's an embarrasment because it's just hard enough to really use day to day, that people who probably ought to - don't.
Mind you most people just don't have the patience to get a few solid spokes in their web of trust. Mostly they just establish a few crosslines here and there to people who knwo them so well they'd trust their identity directly anyway.
So how do we really know kernel.org's key is ... well, itself? If the webserver got mucked with, how do you know this wasn't a target? How do we know our install discs are safe?
Well, we buy them, and they're on a pressed CD, so we know they came from that distro...
Nice try. A lot of people get a free or cheap disc from a less perfect source. And it certainly hasn;t happened to any Linux vendor yet, but in the mswin world an occasional software vendor has mistakenly shipped a trojan or a virus. Being a commercial pressing is good, but isn't really a guarantee.
Commercial distros restrict who can commit to the product release, and that can be considered a good thing. Debian's build servers use GPG to very the identity behind a package sent to them. But what we, the sysadmins and other users, can't be really sure of which build server a given rpm or eb or tarball really came from. Some of the systems allow checking that the download server you have reached is authentic. But if it got sent junk - ouch. I think it even happened to one of the distros once, though they spotted it in very short order.
Build computers should automagically sign packages, the way mail passing through a system gets marked up with a Received: header. In fact the analogy is pretty good - right down to dirty liars forging a few fake ones behind themselves when they want to send junk. But then folks like you and I have to be able to establish that the keys are good. And that process takes human energy.
Why? Because we can't just have the computers randomly make up keys. A person's got to create a key, sign itself, get a few of his buddies to sign the key, really use it. As a web of trust grows, a key identity is well known, and you could say you recognize a given key as good the way many people can recognize a particular actress or other public figure. You gotta hand it to the debian guys for keying with each other so they can be sure of who's sending what... but that's for sending them up to their core servers. The build servers work automatically to crank out official .deb files, but WE can't tell where they were built. Even if the build server did sign these packages (good idea) then how do you and I know the key is trustable. Let's get serious, it's pretty hard to get a silicon lifeform to come to dinner and show you its state ID or some of the other things people do to prove they're themselves. Ok, so the sysadmins sign the key. But you can't just have the key with no passphrase - if you did that, anyone who somehow got to it could steal it, then use it to build wicked packages all they liked. No way. So you end up with a critical system which has to have someone take a look at it and load up the key again if it has to reboot.
Maybe if we have more than a few sysadmins know the fingerprints of these keys that should be so well known, it'd become reasonable to have checkable signed packages. In fact let's go one further, the rules or spec or whatever it is inside a package that makes it something more than a tarball, should be signed by the coder responsible for the package. And if they don't check out we don't care which totally trustable build server built this toy. And let's get these important keys' fingerprints into some places that can't be cracked and spoofed. Get these things into printed manuals, into magazines (maybe just a few at a time, random good ones that the staff have managed to verify), and onto pressed CD covers where applicable.
Okay. Say you've all your ducks in a row and all sorts of things are signed... and verifiable. Everybody knows who everybody is. Then we narrow the field of problems down to the merely ordinary - once you know who's who, then you can really ask yourself if they know what's what or are doing what's right.
But at least you know who you're talking to and who you're getting your bits from.
 linux server for xwindow....need hints
linux server for xwindow....need hintsFrom J. BAKSHI
Answered By: Ashwin N, Jim Dennis, Dan Wilder, Jason Creighton, John Karns, Kapil Hari Paranjape, Thomas Adam
Hi all, I am a faculty at an institute. we use Linux as a server. students telnet to the linux server & use the bash shell from their windows machine. but I am interested to provide them the xwindow system of linux. so is it possible to use the xwindow of the linux server from their client windows machines ? if yes then plz give me some hints or the internet source where I can know the process.
thanks in advanced
[Ashwin] You can install one of the many commercial X servers available.
- HummingBird:
- http://www.hummingbird.com
- WinaXe:
- http://www.labf.com/winaxe
If you want a truly free X server you can use the one that ships with CygWin. As a bonus, your students can try their shell and system programming on CygWin itself. Almost every Linux commandline and programming utility is available on CygWin.
- CygWin:
- http://www.cygwin.com
- CygWin/XFree86:
- http://www.cygwin.com/xfree
- CygWin/XFree86 User's Guide:
- http://xfree86.cygwin.com/docs/ug/cygwin-xfree-ug.html
[JimD] But ... PLEASE, stop using telnet! ssh -X will be far more secure and actually easier to use (if the cygwin version of OpenSSH support X11 forwarding/tunnelling to the cygwin X server). I'd only use the cygwin ssh for the X apps or for very simple commands --- for any curses applications I'd recommend putty. It's terminal emulation is better than any I've seen for MS Windows.
[Dan] X Windows is a client-server arrangement. In the strict sense I use here, "client" means "program which initiates contact with a server" and "server" means "program which provides services when contacted."
In this sense the familiar X programs such as xterm, Mozilla, StarOffice, and so on, are all "clients" and the program which provides display services for these is a "server". To wit, an "X server".
Normally the X server runs on the workstation, while the X clients run on the workstation or elsewhere. In your model, the X clients would run on the Linux server system, while the X servers would run on the Windows systems.
You need an X server for Windows. You're in luck. The most popular X server for Linux, BSD, et al, XFree86, has been ported to Windows and is available as a part of the Cygwin package, developed originally by Cygnus Support, now owned by Red Hat.
Take a look at http://www.cygwin.com and check the "XFree86" link on the front page.
An alternative is the VNC package, http://www.uk.research.att.com/vnc which uses its own client-server arrangement. In this case the X server, "vncserver", runs on the Linux server and proxies the connection over to Windows, where the display is handled by "vncviewer".
Both approaches have their advocates. Both work. YMMV.
[Jason] VNC ("Virtual network computing") can also be found at: http://www.realvnc.com
![]() PS: I know the best solution is to install the Linux at the clients
machines, but the institute will not permit the same. so the only way is to
use the xwindow of the Linux server pc.
PS: I know the best solution is to install the Linux at the clients
machines, but the institute will not permit the same. so the only way is to
use the xwindow of the Linux server pc.
[JimD] We already answered this in other ways, but I just noticed your postscript and wanted to add --- why not use KNOPPIX: http://www.knoppix.net
You could use KNOPPIX CDs, boot the systems up, running X and ssh and a large collection of other Linux software right off the CD. You wouldn't be "installing" anything. KNOPPIX runs from CD and out of the RAM disk.
[John] Knoppix is definitely cool and one heck of a technical marvel. I've been using it for a while for rescue type stuff, and a few other things. And night before last, I decided to install it on my newer Inspiron to get my feet wet with a Debian install - nice easy install - Debian w/o the install / configuration headache!
[Robos] Well, they are working on a better installer, taking over the progeny installer and modifying it. Dunno how far that went though...
[Heather] For very crude values of installer, you can actually install straight from knoppix. knx-hdinstall is the app you're looking for, though it's really a shell script laced with dialog commands.
![]() [John]
One problem I'm having with the install is that I'm unable to run X as a
user I created after the install. The install created a login "knoppix"
and the root of course. Afterward, I created a personal login using the
"useradd" utility, and specified the "-m" switch and that it use a login
shell.
[John]
One problem I'm having with the install is that I'm unable to run X as a
user I created after the install. The install created a login "knoppix"
and the root of course. Afterward, I created a personal login using the
"useradd" utility, and specified the "-m" switch and that it use a login
shell.
[Robos] Take a look at adduser, this is the debian way of adding users and groups to the system and adding users to groups: <quote man adduser> "They are friendlier front ends to the useradd and groupadd programs" </quote>
I created my users on my machine and that of my girlfriend just fine like that. Give it a try!
![]() [John]
However "startx" returns with an error informing me that the login
is not authorized to use the X srvr. I looked through some of the X
related scripts and have combed through some of the Debian docs and links
the Knoppix has set up, but to no avail.
[John]
However "startx" returns with an error informing me that the login
is not authorized to use the X srvr. I looked through some of the X
related scripts and have combed through some of the Debian docs and links
the Knoppix has set up, but to no avail.
Then I deleted the login id via the KDE user mgr utility (w/o deleting the home dir) and re-created. It then let me run X from that account ... until I rebooted the machine, and now I have the same problem. Any insight on that? I've looked through the logs, and couldn't see any clue.
[Heather] Try adding the user to some of the same groups in /etc/group that the user knoppix belongs to?
[Kapil] Since Knoppix is based on Debian it is likely that it uses the Xwrapper program. This is controlled by /etc/X11/Xwrapper.config on a "sarge" version of Debian. This file contains the "allowed_users" option with possible values of "rootonly", "console" and "anybody".
[Thomas] Kapil, you're not wrong, and indeed I actually use Knoppix purely as a rescue CD, preferring my version of Debian Sarge to be pure. Mind you, I might get around to running Knoppix in a chroot jail at some point....
[Kapil] For more details "man Xwrapper.config" is your best bet. Since this file can be managed by "debconf" you could also try to run
dpkg-reconfigure -plow xserver-common
but I am not sure how many changes Knoppix makes to "debconf"-style configuration.
[Thomas] AFAICT, the debconf style intact as one would expect it to be in Debian.
[Thomas] Could the problem also be the "~/.xsession" does not exist? Typically Debain (and other distros) look for this file.... I'd check that that exists and if not do something like...
See attached thomas.dot-xsession.txt
That is my ~/.xsession (chmod 700).
![]() [John]
Indeed it does not exist - in either users home dir, neither the one for
which X functions normally nor the one for it doesn't. There _does exist
what I would assume to be one for global use of all X users on the system.
[John]
Indeed it does not exist - in either users home dir, neither the one for
which X functions normally nor the one for it doesn't. There _does exist
what I would assume to be one for global use of all X users on the system.
It doesn't matter what I put in ~/.xsession, running startx gives the output:
Using authority file /home/jkarns/.Xauthority Writing authority file /home/jkarns/.Xauthority Using authority file /home/jkarns/.Xauthority Writing authority file /home/jkarns/.Xauthority X: user not authorized to run the X server, aborting
![]() [John]
OK, there is an Xwrapper config on the system which contains only the
following:
[John]
OK, there is an Xwrapper config on the system which contains only the
following:
Xwrapper.config
---------------
allowed_users=console nice_value=-10
I discover that if I change 'console' to 'anybody' then X runs. There is remains a caveat with the .Xauthority file, however. It gets written as an empty file, whether or not I'm allowed to run X.
In any event, I'd kinda prefer to use the security mechanism that they're
implementing here and leave it set to 'console'. So it seems that the
problem may lie with the system determining that I'm running starts from the
console. These convoluted X startup scripts give me a headache.
![]()
[Kapil] What is the output of the "tty" command? On my system (/dev is devfs type) the output is "/dev/vc/n" (where n is the number of the virtual console). The wrapper strict says that the "console" keyword stands for any virtual console.
![]() [John]
Output is "/dev/ttyn" where n is the virtcon number ... X runs, even with
the allowed_users set to "console".
[John]
Output is "/dev/ttyn" where n is the virtcon number ... X runs, even with
the allowed_users set to "console".
Ahha, but if I run screen (as I customarily do), then "tty" reports "/dev/pts/n-1" where the number of the term is 1 less than in the ttyn above, and 'startx', fails.
So the problem does lie with the system not recognizing pts as being the console, which is probably correct, as xterms also seem to fall in the domain of "pts". So I guess that for now, the solution will be to "startx" before running "screen".
Thanks for your input.
[John] It's worked wonderfully in almost all situations of booting from the CD. The only exception to date was when I was booting it on some older K6-2 mobos (PC100, a.k.a PC Chips brand) recently. Due to the SCSI emulation mode that Knoppix uses, there was some wierdness where I couldn't access the IDE hd - some kind of compatibility issue - haven't run into that with more recent / better quality mobos. Maybe could have worked around it some way, but didn't have the time to mess with it. Hats off to Mr. Knopper and his associates.
[Robos] You can specify something to the kernel like hda=ide or something. There are the "cheat-codes" which would probably list this, and they are already there at the boot up screen (F1 IIRC)
[John] Another nice venue for me has been the SuSE Live CD distro. Very similar in concept to Knoppix, (not quite as efficient at autoconfiguring the hardware) but with the added feature that it will write a (100 MB) cfg file to an existing FAT filesystem to make the configuration non-volatile. So you can cfg the NIC, routing table, user logins etc., and have it all set for subsequent logins.
[Robos] Like persistent home with knoppix? You have the option to save config and your home to hdd with knoppix too, just RT*M a little

[Heather] Actually, like persistent home plus config floppy. Knoppix seperates the two ideas. And I'm not sure it has any useful support for more than one user account.
[John] Very nice - might be worth a look for the kind of usage that Mr Bakshi is talking about. The Live CD is available (last I checked at least) for free download from the SuSE mirror sites (www.suse.com for U.S.), contrary to their commercial multi-CD distro.
![]() Thanks to all of you, who have helped me by giving the technical hints on
setting a xwindow server.
Thanks to all of you, who have helped me by giving the technical hints on
setting a xwindow server.
I am very grateful to Mr. Dan Wilder for his writing on X server & clients. It has solved some of my confusion.
thanks a lot.
 hard links
hard linksFrom Kathy
Answered By: Jason Creigton, Faber Fedor, Neil Youngman, Jim Dennis, Jay R. Ashworth, Ben Okopnik, Thomas Adam
![]() I'm confused, if Linux doesn't allow directory hard links then why does
every Linux directory have at least two hard links?
I'm confused, if Linux doesn't allow directory hard links then why does
every Linux directory have at least two hard links?
Thanks, Kathy
[Jason] Not exactly sure....but http://www.linuxgazette.com/issue35/tag/links.html makes for good reading.
[Faber] You know, I'm confused too! Looking into it a little bit, it seems that whether or not directory hard links are allowed depends on the underlying file system. Fire systems that are of type vxfs (no, I don't know what that means either
don't allow the creation of directory hard links. I've yet to discover why.
The reason we have them in Linux (. and ..) is, I always assumed, so we have a way to travel up the directory tree (cd ..), otherwise the system would need to know the name of the parent directory (as opposed to just its inode).
Why is . a hard link to the current directory then? <shrug> Because un*x people are lazy typists?
A very interesting question, BTW. I'm interested in finding the answer to it myself.
[Jim]
The system uses hard links to manage the link from the parent to the directory's inode, the . link in that directory and all of the .. entries in all of its subdirectories.
USER'S (including 'root') are forbidden to create additional hard links because this would make fsck much more difficult to implement and it might allow one to create hard link loops, and dangling sub trees.
Basically the directory linkages are maintained by the filesystem to glue the whole tree together, to ensure that it is truly an acyclic tree structure with a single root.
In other words it's a policy enforced by the kernel. Some other UNIX systems have allowed root to create hardlinked directories; and it could be done with a disk editor like LDE under Linux (though I'd expect fsck to complain the next time it was run --- and if you did something degenerate you might cause some interesting problems --- possibly even cause the kernel to treat the fs as corrupt and invoke it's handler (remount,ro, panic, or continue) and possibly even cause some kernel threads to run amok or panic the system.
[Neil]
Traditionally, in Unix systems a file or directory is physically deleted from the disk when there are no hard links to it. The rm and rmdir commands command remove a directory entry (link). If there are more than one hard links to a file or directory, the file remains, so although we regard the rm command as deleting a file, it only deletes the link to the file. When there are no hard links to a file or directory, the file system will then free up the actual space used by the file. There have to be hard links to directories or they would be deleted by the filesystem.
ISTR that hard links to directories can only be created by mkdir to ensure that we can't build up cyclic directory structures, otherwise programs such as find, which traverse the directory could loop over the same directory structure for ever.
In conclusion, Linux does allow hard links to directories, but it only allows hard links to a directory from itself and it's parent directory. These are the two hard links to which you refer.
[Neil] Some ambiguity there. If there are more then one links before the rm command, there will be at least one after the rm command, so the file space isn't freed. Of course rmdir deletes both links to a directory.
[Jason]
Okay, I've looked into this more: It appears that, for some reason or another (Another Gang member will no doubt know why) it's a Bad Idea to make hard links with directories. Look here:
root:~# ln lala foo
ln: `lala': hard link not allowed for directory
root:~# strace ln lala foo
execve("/bin/ln", ["ln", "lala", "foo"], [/* 17 vars */]) = 0
uname({sys="Linux", node="jpc.example.com", ...}) = 0
brk(0) = 0x804db0c
open("/etc/ld.so.preload", O_RDONLY) = -1 ENOENT (No such file or
directory)
open("/etc/ld.so.cache", O_RDONLY) = 3
fstat64(3, {st_mode=S_IFREG|0644, st_size=19148, ...}) = 0
mmap2(NULL, 19148, PROT_READ, MAP_PRIVATE, 3, 0) = 0x40014000
close(3) = 0
open("/lib/libc.so.6", O_RDONLY) = 3
read(3, "\177ELF\1\1\1\0\0\0\0\0\0\0\0\0\3\0\3\0\1\0\0\0\20\\\1"..., 1024) =
1024
fstat64(3, {st_mode=S_IFREG|0755, st_size=1494904, ...}) = 0
mmap2(NULL, 1256324, PROT_READ|PROT_EXEC, MAP_PRIVATE, 3, 0) = 0x40019000
mprotect(0x40144000, 31620, PROT_NONE) = 0
mmap2(0x40144000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED, 3,
0x12a) = 0x40144000
mmap2(0x4014a000, 7044, PROT_READ|PROT_WRITE,
MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x4014a000
close(3) = 0
mmap2(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) =
0x4014c000
munmap(0x40014000, 19148) = 0
stat64("foo", 0xbffffc10) = -1 ENOENT (No such file or
directory)
lstat64("lala", {st_mode=S_IFDIR|0755, st_size=48, ...}) = 0
write(2, "ln: ", 4ln: ) = 4
write(2, "`lala\': hard link not allowed fo"..., 43`lala': hard link not
allowed for directory) = 43
write(2, "\n", 1
) = 1
exit_group(1) = ?
Notice, that, in the strace output, link() doesn't actually get called. So is this 'ln' just trying to save us from outselves, or is the kernel or glibc? I wrote this quick C program:
See attached creighton.c-link.c.txt
root:~# link=/home/jason/prog/c/link
root:~# $link lala foo
Error while linking: Operation not permitted
root:~# strace $link lala foo
<sniped syscall trace that looks very similar to ln's strace output....the
important line is:
link("lala", "foo") = -1 EPERM (Operation not permitted)
<sniped more>
root:~#
So, 'ln' sees that you're trying to hardlink directories and doesn't even attempt it, instead giving a useful error message. And since we see the link() syscall being proformed, it means that the kernel doesn't allow hard linking of directories, and it's not the glibc wrapper that refuses to hardlink directories. (If it had been glibc, we would not have even seen link() being called: the link() in glibc would have returned without calling the link() syscall.)
Now, back to your original question: I have no idea why creating hard links to directories is a bad idea. (It must be, or Linux would allow root to do it.) LG #35 Answer Guy column has something about this: (Quoting from the article I linked to in my other email)
<quote>
Some versions of Unix have historically allowed root (superuser) to create hard links to directories --- but the GNU utilities under Linux won't allow it --- so you'd have to write your own code or you'd have to directly modify the fs with a hex editor
<end quote>
Well, obviously, it's the kernel disallowing it, not GNU utilites. However, LG
#35 was some time ago, so things might have been different then.
[jra]
User-added hardlinks to directories are forbidden because they break the directed acyclic graph structure of the filesystem (which is an ASSERT in Unixiana, roughly), and because they confuse the hell out of file-tree-walkers (a term Multicians will recognize at sight, but Unix geeks can probably figure out without problems too.
(Did I get that right, Ben?
And indeed, anyone who's ever done
# rm -rf .*
in a user's home directory to clear out all the dotfiles prior to dropping the user will no doubt understand why even the system 3 links to a directory (. in ., .. in children, and the named link in the parent) are often 2 too many.
[Jason]
Ouch! Never thought about that, I'll have to remember that....
[Jason]
Yes, I wrote that before I got to read the rest of the thread. With symlinks, at least it's easy to tell when there's a loop. (BTW, I seem to recall an option in Wine to ignore symlinks because they causes some Windows programs to get very, very confused.)
~/tmp$ ln -s file1 file2
~/tmp$ ln -s file2 file1
~/tmp$ ls -l file*
lrwxrwxrwx 1 jason users 5 Jul 20 16:59 file1 -> file2
lrwxrwxrwx 1 jason users 5 Jul 20 16:59 file2 -> file1
~/tmp$ cat file1
cat: file1: Too many levels of symbolic links
~/tmp$ strace -e trace=open cat file1
open("/etc/ld.so.preload", O_RDONLY) = -1 ENOENT (No such file or directory)
open("/etc/ld.so.cache", O_RDONLY) = 3
open("/lib/libc.so.6", O_RDONLY) = 3
open("file1", O_RDONLY|O_LARGEFILE) = -1 ELOOP (Too many levels of symbolic links)
cat: file1: Too many levels of symbolic links
[jra] User-added hardlinks to directories are forbidden because they break the directed acyclic graph structure of the filesystem (which is an ASSERT in Unixiana, roughly), and because they confuse the hell out of file-tree-walkers (a term Multicians will recognize at sight, but Unix geeks can probably figure out without problems too.
[Jason] I just thought of something else:
Disk space management and memory management are the same thing.
UNIX has chosen reference counting for disk space management. Reference counting can't deal with cyclic (Right word? I mean data structures that refer to themselves.) data structures, and thus hardlinking directories is disallowed. If Linux used garbage collection, it would be okay to hardlink directories, if very confusing.
But using GC on filesystems would be slow and offer no real advantages, so reference counting is okay.
![]() Well, root must be able to create hard links,
because of the option ln --directory (-d, -F).
Well, root must be able to create hard links,
because of the option ln --directory (-d, -F).
[Jason] Try it:
root:~# mkdir dir1 root:~# ln -d dir1 dir2 ln: creating hard link `dir2' to `dir1': Operation not permitted
![]() [Thomas]
Then in the same thead....
[Thomas]
Then in the same thead....
![]() [jra]
And indeed, anyone who's ever done:
[jra]
And indeed, anyone who's ever done:
# rm -rf .*
[Jim]
The GNU version of 'rm' will refuse to attempt recursion into or unlinking of . and/or .. entries.
However this is still a classic sysadmin tech question. It's almost as common as: "How do I remove a file named -fr?"
[Ben]
rm -- -fr rm ./-fr perl -we'unlink "-fr"' "F8" in Midnight Commander
[Thomas]
You forgot to mention using Emacs.... You also didn't mention jettisoning the disk into space...
[Jim]
How do you SAFELY remove all the dot files and dot directories under the current directory?
My best answer under Bash is:
rm -fr .??* .[^.]
[Ben]
rm -rf .[^.]*
is what I've always used; this would, of course, ignore files named "..." and so on, but that's not much of an issue in practice.
[Jim]
... this gets anything starting with a dot and followed by at least two more characters (thus . and .. won't match) and also it gets anything starting with a dot and followed by any single character other than a dot (thus getting such unlikely entries as .a .\? etc). This pair of glob patterns should match every possible dot entry except . and ..
However, I preface it with under bash. I happen to know it will work under ash, zsh, tcsh, and most other modern shells. However, if I was on a particularly old shell I'd have to check. The negated character class might not have been in the glob libraries of earliest Bourne and C shells.
If I really had to write a script for maximum portability:
rm -fr .??*; rm -fr `echo .? | grep -v '\.\.' `
... remove all the longer dot entries in the obvious way, then let echo match all the two character dot entries and grep out the .. entry explicitly.
[Ben] Other interesting situations come up when you want to delete a file named in a foreign language. I've run into a Russian song name that even Midnight Commander couldn't handle. Cutting and pasting to "rm" didn't help either (clearly, some of the characters were the "escaped" types, but I had no idea which ones - long story short, the machine didn't have any Russian fonts on it.) Even "ls -b" failed for the above, for whatever reason. I ended up doing something like
perl -wle'/match/&&print for <*>'
where "match" was a small substring of the characters in the name. Needless to say, "print" became "unlink" when I saw that only the appropriate file matched.
 entering into the interactive mode
entering into the interactive modeFrom Joydeep Bakshi
Answered By: Thomas Adam, Heather Stern, Kapil Hari Paranjape, Jason Creighton
![]() Hi all,
I can enter into the interactive mode of Redhat by pressing key i at the
time of booting. but this technique doesn't work in Debian . how to get the
same thing in Debian ?
Hi all,
I can enter into the interactive mode of Redhat by pressing key i at the
time of booting. but this technique doesn't work in Debian . how to get the
same thing in Debian ?
Please let me know.
thanks in advanced.
[Thomas] Joydeep,
Permit me to make an observation if I may, but this is not the first time that you have tried to emulate RH functionality within Debain. I am all too familiar with RH's "i" startup, and to try and do this in Debian would require a complete re-write of the /etc/init.d/* run-level files, not to mention /etc/iniitab and a complete re-write of "update-rc.d". In short, YOU CAN'T!
[Heather]
Actually, you do it in Debian in a way that works in every single distro that has a sysV-like init sequence (in fact, this would work fro RH, as well) --
Go into runlevel 1 (single user mode)
'sulogin' if needed, but anyways you are at a root prompt.
Walk one at a time through the sequence of commands that would be run on the way to the normal runlevel. This is the number next to "initdefault" in /etc/inittab. In Debian this is, curiously, runlevel 2. Most others use 3 if they mean text mode, 5 if they mean GUI, which are mostly holdovers from Solaris, where runlevels are travelled through, not jumped into. In an untweaked Debian 2 through 5 are all little clones anyway, 2 is just the earilest "normal" runlevel.
Essentially a human traversal of the autoexec sequence. This is much more throough about being interactive than RH's "I" mode, which I suspect skips a few things.
Anyways, I could easily imagine you having hacked the fairly ignored "runlevel 4" to point at a "debug" copy of the /etc/init.d directory, where every script asks if it's okay before running its partner in /etc/init.d. This would not entail hacking inittab (except if you want that the default, annoying behavior) nor update-rc.d (though you would have to USE it once per script flavor to establish that it's not in control of the links in runlevel 4), but whenever a truly new app added something to init.d, you'd need to tweak runlevel 4 to be its proper companion. Hmm, if the "ask if ok" script is generic enough to check its own linkname, it could in fact be only one script. So that's your contribution to the thread, Joydeep, I'd love to see it, and maybe it can be added to the debian system's ordinary utilities.
You could also use runlevel 7, 8, or 9, which are not in the spec for init, but work because it was easier to simply accept numerics than fuss over this minor detail. I believe but would have to test, I don't think update-rc.d gratuitously adds anything to these extra runlevels. BUT BEWARE since they are not normal they also aren't listed among the runlevels that have getty access in /etc/inittab. I'd recommend adding at least one getty console.
[Thomas] My advice is that you cannot have the best of both worlds in this instance. Either you go back to using RH (with apt4rpm) installed or you switch to using Debain and do things the Debain way!
[Heather]
Debian does not require you to do things the debian way, it's just a bunch of planned structure...
Lots of otherwise fanatic debsters use their own kernels, not "the debian way" which is make-kpkg to cook up .deb files, then install those, and let debconf handle lilo. Me, I do way too much dev work on kernels intended for others to allow it to manage my boot sequence. I keep one debian stock kernel as a failsafe and that satisfies "lilo needs kernel-image".
Certainly, one could install any useful distro, then wipe its packaging system out (cleans a lot of space from var) and thereafter ONLY use source from known projects. But this ruins the provided means to get at sources and binary packs optimized for your setup.
[Thomas] Debian handles rc.d files better than any disrto I have used. I'm going to stop with plugging Debian now, in risk of starting a war...
[Jason] Couldn't you just drop a script in /etc/rc4.d (or whatever the right directory is), name it "S00askifok", and have it loop over scripts in /etc/rc2.d/, asking if it's okay to run each one? Or am I missing something?
[Kapil] I am not sure what RH's "interactive" mode does but if it just asks you whether or not to run a script before running it then it is not really all that complicated to do in Debian. All the start-stop scripts are run from /etc/inittab by a master script /etc/init.d/rc which is what you need to edit.
The actual running of the commands is done at the very end of the script after creating a "command-list" called CMDLIST. This list is run by calling "sh -c $CMDLIST". You could either:
1. Modify /etc/init.d/rc to run the CMDLIST differently (and
interactively). (Allows you to see what each script has done before deciding on the next step). or
2. Modify /etc/init.d/rc to create the CMDLIST interactively. (This way you only need "minor" hacking of the script).
Save the changed script as /etc/init.d/rc.RH and change /etc/inittab to use this script instead of /etc/init.d/rc.
You could even make this fancier and make it save the answers as a runlevel of your choosing.
Hope this helps. If you really insist I could try to hack up versions of these scripts.
 SuSE 8.2 Linux Distribution and Soundblaster 16
SuSE 8.2 Linux Distribution and Soundblaster 16From Chris Gianakopoulos
Answered By: Benjamin A. Okopnik, Chris Gianakopoulos, Kapil, Jason Creighton, Les Baron
Hello Gang,
[Ben] Hey, Chris!
![]() Here is my final observation with the lates SuSE 8.2 Linux distribution.
I have a Creative Labs Soundblaster 16 (not a clone but the real thing),
and the YAST2 configuration tool does not properly set the hardware up
properly (or it does and the chosen driver does not interoperate properly
with my card). The user will be led to believe that the card is set up
but, no sound will be heard from the speaker. Yes, I even played with the
volume control (via the mixers).
Here is my final observation with the lates SuSE 8.2 Linux distribution.
I have a Creative Labs Soundblaster 16 (not a clone but the real thing),
and the YAST2 configuration tool does not properly set the hardware up
properly (or it does and the chosen driver does not interoperate properly
with my card). The user will be led to believe that the card is set up
but, no sound will be heard from the speaker. Yes, I even played with the
volume control (via the mixers).
When I did a cat on /dev/sndstat, there was an the DSP and some other thing that I cannot remember were not activated. Rather than wrestle with things, I created the following script to activate the sound stuff.
#!/bin/bash /sbin/modprobe sb io=0x220 irq=7 dma=1 dma16=5 mpu_io=0x330
[Ben] You could also do this by simply entering the module name and parameters into "/etc/modules". Everything in there gets auto-loaded (at least under Debian - SuSE might be a bit different) by "/etc/init.d/modutils" on startup. In fact, IIRC, I had this exact entry - params and all - on my old laptop.
echo "sb io=0x220 irq=7 dma=1 dma16=5 mpu_io=0x330" >/etc/modutils
No need for a separate script.
It is worth pointing out that Debian's module management relies on the module name appearing in '/etc/modules', and the options going in '/etc/chandev.conf' -- Thomas Adam
![]() Note that I am using the module sb.o rather than the other one (I think that
it was sb_16.o) that YAST2 chose. Normally irq=5 is the common setting; I
chose irq=7. The other parameters are fairly standard for a soundblaster.
Note that I am using the module sb.o rather than the other one (I think that
it was sb_16.o) that YAST2 chose. Normally irq=5 is the common setting; I
chose irq=7. The other parameters are fairly standard for a soundblaster.
One caveat here is that some paralell ports also operate on IRQ's 5/7 and if one is not careful you could get a conflict. -- Thomas Adam
![]() This information is also available in
This information is also available in
/usr/src/linux/Documentation/sound/Soundblaster
That's all!
[Chris Gianakopoulos] Thanks Ben! I tried that too. I was toiling whether or not to just put the entry into /etc/modules.conf. That's how my previous distribution (SuSE 6.4) did it, and that way worked also. The new distribution did not have all of the sound card entries in /etc/modules.conf, so I was scared to put my stuff in. <also grinning>I keep my old distribution manuals because they still have lots of good info (especially pertaining to modprobe).
I'm gonna try your (and standard) way of doing it!
[Ben]
Well now... "modules.conf" is a different animal altogether. I've tweaked it a couple of times via all the crud under "/etc/modutils" and running "update-modules", but I can't say that I like it much or even trust the damn thing. It's too apt to bite.
Oh, I don't know that it's the standard way - although it may be - but it's what I've been using for a number of years now, and it works. Other than the modules.conf mechanism, I don't see the whole module-loading thing as being all that complex.
![]() Ahhh yes. We'll give it a test and see what happens. I've had pretty good
luck in the previous distribution (SuSE 6.4).
Ahhh yes. We'll give it a test and see what happens. I've had pretty good
luck in the previous distribution (SuSE 6.4).
You're right. The module-loading is cool. The more that I learn the less black magic things appear to be. It gets simpler and simpler as I use Linux more and more. Of course, Linux is not black magic. It's a work of art!
continuting on similar lines.... -- Thomas Adam
[Kapil] The recent kmod/ptrace bug seems to indicate that the "coolness" of autoloading kernel modules (a la /etc/modules.conf) comes with a price. It is probably safer to load modules at boot time using "/etc/modules" and then turn off modprobing with using kernel capabilities or some other mechanism.
Of course, you can continue autoloading if (a) you apply the relevant patch to Linux 2.4.20 or (b) if your machine is not in danger of attack from local users or (c) security is not an issue
[Ben] Sorry to hear that you got bitten. Someone on Bugtraq suggested what seems like a really good solution to the whole ptrace() problem when it originally came up - add a single line to the kernel that fails out of the call if the user is not part of group "ptrace". This seems like it would be trivial to implement, and would be transparent to the average casual user.
[Jason] Interesting, but how would the kernel know what uid is in the "ptrace" group? Something in the /proc filesystem?
[Chris]
I think that SuSE fixed the ptrace problem in their 8.2 distribution. The source of that info is at
http://linuxtoday.com/security/2003032502126SCKNSS
It will be interesting to look at the kernel source to see if the fix is really there.
[Ben] Nope - via the standard permissions mechanism. It's all easily accessible; take a look at "Reading the Persona of a Process" in "libc.info".
Some folks thought that only UID0 should have access to "ptrace", but I thought this method gave a lot more flexibility while maintaining a good level of security. It still takes root to add a user to a group.
[Jason] But user group names are purely userspace, right? So the kernel has no idea that the name of group X is. So, we either force "ptrace" to be a certain group ID (Not a very good plan) or somehow have it configurable, probably via the /proc filesystem.
[Ben] I don't think it would be all that difficult to do a lookup in "/etc/groups" - not that I remember it being proposed that way. I don't remember the exact code snippet that the guy showed, but it was only two or three lines long. If I had faster access, I'd go dig around on securityfocus.com and pull it up for you. You might want to give that a shot yourself; shouldn't be too difficult.
[Jason] That not the point! An easy way to win any argument is to claim "that's not the point" over and over again, even when it is the point.

Seriously, it would be ugly to introduct a lookup like that into the kernel: AFAIK, the kernel does not currently depend on anything like that in userspace, save for a few things, which are configurable. (Like the path to the modprobe binary.)
I've cut a fair chunk of this thread out, and Heather may well pull rank on me and get me to include it!!Suffice to say, I have left out various ptrace() rants and people eating meat..... -- Thomas Adam
[Les Baron]
Hi SuSE generally uses alsa, have you tried alsaconf on the commandline??
[ChrisG]
I don't think that I did on my desktop. I think that the only thing that I tried was Yast2. I'm pretty sure that Yast2 uses alsaconfig to detect my sound card which I know that could not be achieved automatically. I will give alsaconfig a try.
[Les Baron]
Typing alsaconf in a terminal will bring up a dialogue ad ask you about your card it is seperate to Yast2 and is included in the alsa package, there have been times when I have upgraded alsa (not in an rpm format) and yast2 no longer recognizes my SoundBlaster live however alsaconf sets it up.
This is because YAST2 relies on its own stock version to interface to the YAST modules provided by SuSE -- Thomas Adam
[ChrisG]
I tried alsaconfig about a half an hour ago. It recognized my legacy card configured /etc/modules.conf, and even started its sound stuff. I was able to use wavplay and listen to different wave files. Cool! Then, when I rebooted the system, the sound did not work! Darn! I have to investigate the difference between the startup via alsaconf and the way things happen when booting the system.
The modules do load when using wavplay with .wav files (I know - I can just cat the file to /dev/dsp, I think), but no sound occurs. One might ask which modules get loaded? Do all of the ones that I need get loaded? I will investigate and figure out answers to those questions. I could just use my existing sb.o stuff, but I do have a challenge to conquer!
[Les Baron]
The sound card is muted when you first configure alsa you will need to start a mixer and adjust the volume. You can also stop and start alsa by typing rcalsound stop or start.
The common mixer that is used is 'aumix' and is shipped with SuSE and Debian. It is not always necessary to use a mixer however, as doing something like:
cat randomfilethatisnotanywhere > /dev/dsp
will also activate your soundcard. -- Thomas Adam
 Kernel Compiling and Framebuffer Device
Kernel Compiling and Framebuffer DeviceFrom Priit Kivisoo
Answered By: Benjamin A. Okopnik, Thomas Adam
Hello.
I have a problem compiling kernel (2.2.19 currently) on Debian GNU/Linux 2.2r6. Every time I compile it, after rebooting, I get messages like:
depmod: *** Unresolved symbols in /lib/modules/2.2.19/sound/sound.o
[Ben]
It sounds like the modules are not being installed after the kernel compilation. I've seen the "standard procedure" fail to do so unless the original modules subdirectory was renamed or deleted. So, for those times when you're not sure what's going on, here's Ben's Patented Kernel Recompile with Tasty Module Sauce on top (all done as root, of course):
See attached ben-compilekernel.txt
This assumes that you only have the one kernel source tree installed - obviously, you'd need to "cd" to the appropriate source directory if you have more than one - and that your current kernel version is the same as the one you're running (if it's not, ignore the "version" variable and type out the right numbers.) I'm also not showing any of the output for clarity's sake.
[Thomas] I am wondering whether or not your "modules.dep" file is up to date. As "root", issue:
depmod -a
just to be safe.
Sound support is usually loaded via a module and those settings are stored in "/etc/modules.conf". Check that those settings are accurate for your card. As you are running Debian, take a look at:
man \1 update-modules
[Ben] Good point, Thomas! Although that's supposed to happen automatically during boot (Debian does it via "/etc/init.d/modutils"), it could fail, or not run for some reason. If you see a whole bunch of error messages when you do the above,though, chances are that you've got a mismatched between your kernel and modules.
![]() Also, I was wandering, if someone can tell me, why can't I
use framebuffer device using 32k, It works only with 256 colours
for me... When I use 32k (or 16k), I can't see the cute penguin, not
mentioning X (well, I use XFree86 3.3.11, which came with the distribution,
I have ATI Rage Fury Pro AGP, which SuperProbe can't detect - any
suggestions to that? XFree86 4.* on Slackware 8.0.0 can't recognize
it either...). I get message:
Also, I was wandering, if someone can tell me, why can't I
use framebuffer device using 32k, It works only with 256 colours
for me... When I use 32k (or 16k), I can't see the cute penguin, not
mentioning X (well, I use XFree86 3.3.11, which came with the distribution,
I have ATI Rage Fury Pro AGP, which SuperProbe can't detect - any
suggestions to that? XFree86 4.* on Slackware 8.0.0 can't recognize
it either...). I get message:
Fatal server error: fbdevScreenInit: unableto set screen params (Invalid argument)
At press time, I was unable to reply back to this e-mail. I think the above error message is as a result of bad modelines that the kernel cannot handle. -- Thomas Adam
![]() Oh, btw, framebuffer worked perfectly on Slackware 8.0.0 - even
1024x768x32k worked fine... And Debian 2.2r6 didn't have framebuffer
compiled in kernel, I compiled it myself - maybe I did something wrong,
even though I tried to follow the 'Framebuffer-HOWTO'.
Oh, btw, framebuffer worked perfectly on Slackware 8.0.0 - even
1024x768x32k worked fine... And Debian 2.2r6 didn't have framebuffer
compiled in kernel, I compiled it myself - maybe I did something wrong,
even though I tried to follow the 'Framebuffer-HOWTO'.
[Ben]
Sorry, framebuffer is outside my area of expertise. Someone else here might be able to help, though.
[Thomas]
Well, I might
Framebuffer support is in the experimental part of the kernel, so you have to enable "experimental" in Code Maturity Options (as I assume you have).
If you are using Lilo, make sure that your "vga=" line for the appropriate stanza is set like this:
vga=0x317
Then run "/sbin/lilo"!!!! That'll give you 1024x786x16 colour bit.
![]() Also, I just have to say, that You all at the Gazette, have done
a great job in helping Linux users worldwide... Thank You for that!
Also, I just have to say, that You all at the Gazette, have done
a great job in helping Linux users worldwide... Thank You for that!
[Ben] <smile> Thank you, Priit! Much appreciated, and glad you're enjoying the Gazette.
![]() PS! Sorry about the following ad-s from hot.ee, because
I didn't have any mail client available... sry.
PS! Sorry about the following ad-s from hot.ee, because
I didn't have any mail client available... sry.
[Ben] Hey, Estonian ads. Cool. Don't think I'd seen those before... when I passed through Tallinn 30+ years ago, they didn't have those yet.
I'm
 Question about Laplinking
Question about LaplinkingFrom Steve Michaelis
Answered By: Robos, Jim Dennis, Thomas Adam
Hey, I recently bought a IBM thinkpad 760L with a 75mhz processor. I want to install LibraNet linux on it, but it has no CD and no Network card. I have libranet on my PC and I love it. I was wondering how (or if) I could use the "Null modem laplink" thing that I have heard about. Any help is appreciated! Thanks, Steve
[Robos] This above sucks! Please send plain text, this is all I need to read...
Hmm, word wrapping at 75 chars would be nice too... Anyway, if I'm not too much mistaken libranet is a modded debian version. Soo, you can either look for boot floppies from libranet or use the debian ones and then somehow update to libranet. OK, you loose the advantage of the libranet installer (which is nice if I read it correctly somewhere) but you have it. For instructions on how to install look through these:
http://www.linux-on-laptops.com/ibm.html
[JimD]
In regards to your laplink question: Linux can use a driver called PLIP to provide IP service over a Laplink(TM) type parallel port cable. You basically just:
modprobe plip ifconfig plip1 $IPADDR pointopoint $OTHERADDR route add default plip1
and you can using any normal TCP/IP protocol over the resulting link, just like it was a PPP link but over a parallel port rather than a serial line.
[Thomas] Jim -- it is well publicised that I run PLIP due to lack of NIC's. While your instructions above are perfectly accurate, they may well not work.
The command "modprobe plip" assumes that certain settings have been set in /etc/modules.conf. In debian the command "update-modules" does a relatively good job of this, but I still find editing the file by way of "vim" a necessity, if not for my own sanity.
The module "plip" replies on "parport" and "parport_pc" (often a module alias) to be loaded. This is usually done anyway if you have a paralell port on your machine.
One thing that plip will require is to know the irq and the io address of your paralell port. Thus, in my /etc/modules.conf I have the line:
alias parport_lowlevel parport_pc options parport_pc io=0x378,0x278 irq=7,auto
Which assumes that the paralell port uses an IRQ of 7 (typically 7 + 5 are the usual IRQ's). You should also ensure in your BIOS that the paralell port mode is set to something like EPP or Bi-directional.
[JimD]
I know know of a Linux installation floppy that supports this. However, I imagine with enough sweat and work, you could trick a Toms Root/Boot floppy into running it; then mounting NFS off another Linux box, running ldconfig to access a more recently and full features glibc, partition, format and mount your filesystems, and run debootstrap on that.
It would take a Linux expert. I just used debootstrap to install Debian onto my laptop (using LVM, logical volume management). It took about thirty steps
I know know of a Linux installation floppy that supports this. However, I imagine with enough sweat and work, you could trick a Toms Root/Boot floppy into running it; then mounting NFS off another Linux box, running ldconfig to access a more recently and full features glibc, partition, format and mount your filesystems, and run debootstrap on that.
It would take a Linux expert. I just used debootstrap to install Debian onto my laptop (using LVM, logical volume management). It took about thirty steps. (My experience is documented at my Wiki site: http://www.starshine.org/SysadMoin/moin.cgi/DebootstrapInstallation )
Your situation would be even trickier.
However, it's possible you could simply pull out the hard drive, temporarily install it into a desktop system, install Linux there (leaving it mostly unconfigured) and then re-attach the hardrive into the laptop). This is also tricky and requires some expertise. Heather (my wife) is a pro at that technique.
Sorry I can't be more detailed, but this should just give you the basic ideas.
|
...making Linux just a little more fun! |
By Michael Conry |
|
Contents: |
Submitters, send your News Bytes items in PLAIN TEXT format. Other formats may be rejected without reading. You have been warned! A one- or two-paragraph summary plus URL gets you a better announcement than an entire press release. Submit items to bytes@linuxgazette.com
 August 2003 Linux Journal
August 2003 Linux Journal
![[issue 112 cover image]](misc/bytes/lj-cover112.png) The August issue of Linux
Journal is on newsstands now.
This issue focuses on Security. Click
here
to view the table of contents, or
here
to subscribe.
The August issue of Linux
Journal is on newsstands now.
This issue focuses on Security. Click
here
to view the table of contents, or
here
to subscribe.
All articles older than three months are available for
public reading at
http://www.linuxjournal.com/magazine.php.
Recent articles are available on-line for subscribers only at
http://interactive.linuxjournal.com/.
Joseph Pranevich's Wonderful World of Linux 2.6. Longish, but very detailed and a pleasure to read.
![]() The E-zine
LinuxFocus:
has for July/August the following articles:
The E-zine
LinuxFocus:
has for July/August the following articles:
An overview of Linux's future on the desktop [PDF], commissioned by Mitch Kapor of the Open Source Applications Foundation is available online. It includes a checklist of things Linux needs to take a quantum leap in penetrating the desktop.
A couple of links from the O'Reilly stable:
Computer know-how spreading in Afghanistan: Atia Jeewa writes "The first class of 11 Afghan civil servants trained in Linux operating systems returned to work this week after completing a 10-day certification course supported by the United Nations Development Programme (UNDP)."
Some links of interest from Linux Weekly News:
Some links highlighted by LinuxToday:
Some links of interest from NewsForge:
The Linux Router project is dead.
The Mercury News have interviewed Linus Torvalds.
Links of interest from The Register:
Dyne:bolic: A broadcast studio on a Linux CD. This Linux distribution promises to provide a multimedia studio -- complete with the ability to transmit Webcasts worldwide -- without ever installing any software on your hard drive.
Tim O'Reilly on why software licenses don't work, and Slashdot comments on the topic.
Listings courtesy Linux Journal. See LJ's Events page for the latest goings-on.
|
12th USENIX Security Symposium |
August 4-8, 2003 Washington, DC http://www.usenix.org/events/ |
|
HP World |
August 11-15, 2003 Atlanta, GA http://www.hpworld.com |
|
Linux Clusters Institute Workshops |
August 18-22, 2003 Yorktown Heights, NY http://www.linuxclustersinstitute.org |
|
LinuxWorld UK |
September 3-4, 2003 Birmingham, United Kingdom http://www.linuxworld2003.co.uk |
|
Linux Lunacy Brought to you by Linux Journal and Geek Cruises! |
September 13-20, 2003 Alaska's Inside Passage http://www.geekcruises.com/home/ll3_home.html |
|
Software Development Conference & Expo |
September 15-18, 2003 Boston, MA http://www.sdexpo.com |
|
PC Expo |
September 16-18, 2003 New York, NY http://www.techxny.com/pcexpo_techxny.cfm |
|
COMDEX Canada |
September 16-18, 2003 Toronto, Ontario http://www.comdex.com/canada/ |
|
IDUG 2003 - Europe |
October 7-10, 2003 Nice, France http://www.idug.org |
|
Linux Clusters Institute Workshops |
October 13-18, 2003 Montpellier, France http://www.linuxclustersinstitute.org |
|
LISA (17th USENIX Systems Administration Conference) |
October 26-30, 2003 San Diego, CA http://www.usenix.org/events/lisa03/ |
|
HiverCon 2003 |
November 6-7, 2003 Dublin, Ireland http://www.hivercon.com/ |
|
COMDEX Fall |
November 17-21, 2003 Las Vegas, NV http://www.comdex.com/fall2003/ |
|
Southern California Linux Expo (SCALE) |
November 22, 2003 Los Angeles, CA http://socallinuxexpo.com/ |
|
Linux Clusters Institute Workshops |
December 8-12, 2003 Albuquerque, NM http://www.linuxclustersinstitute.org |
 Intrinsyc Begins Shipping Linux-based CerfCube PPC 405EP
Intrinsyc Begins Shipping Linux-based CerfCube PPC 405EP
Intrinsyc Software International, a global provider of specialized, intelligent devices, today announced it is collaborating with IBM Microelectronics on the marketing of its IBM PowerPC 405EP embedded processor using Intrinsyc's new CerfCube 405EP reference platform.
Ideal for server appliances, data collection devices, scanners, and Internet-enabling machines, the CerfCube 405EP is also suited for network routers and concentrators, LAN-based video, wireless networking access points, and any application requiring the movement of significant amounts of data over a LAN. The full press release is available online.
 ERP5 and Collaborative Portal Server (CPS) Teams Form Alliance
to Provide World First Global Open Source Information System
ERP5 and Collaborative Portal Server (CPS) Teams Form Alliance
to Provide World First Global Open Source Information System
ERP5 and Collaborative Portal Server teams announced at the Libre Software Meeting (LSM) international conference on Open Source / Free Software that they would join forces to provide the world first global Information System exclusively based on Open Source / Free Software. Collaborative Portal Server (CPS) is a content management and collaborative work system published under GPL license with more than 100 production instances implemented in large governmental organisations and very large industrial organisations. ERP5 is the first Entreprise Resource Planning system published under GPL license with successful implementation in European industry. The Alliance of ERP5 and CPS will provide corporations with seamless integration of collaborative and quantitative information systems based on the Zope Open Source / Free Application Server.
ERP5 allows to track quantitative information and implement management workflows. ERP5 features covers trading, invoicing, accounting, manufacturing, supply chain, stock, customer relation and product design.
CPS allows a group of users to share documents in multiple versions, implement administrative and publication workflows and create a single point of access to corporate information and services.
 Free Software integrated solution for Governments
Free Software integrated solution for Governments
A Free Software System know as "GONUX" was launched on July 1st by the Free Software Consortium, a global organization dedicated to the promotion and commercialisation of free software.
GONUX is a compilation of programs widely used by public sector offices in Brazil, Argentina and Spain. It contains the GNU/Linux Operating System and server, Open Office, email and instant messenger, a calendar, a database, a web browser application and many other programs. GONUX is meant to be a common free government operating system platform for public sector offices worldwide, both server and client-side.
To obtain a full version of GONUX visit gonux.fsc.cc and register for it.
 IO Anywhere Announces new Linux appliance
IO Anywhere Announces new Linux appliance
IO Anywhere Inc. has announced the release of its first generation product. IO Anywhere started with a mission to develop an appliance that cost less than $200, had to have lots of onboard I/O, multiple serial ports, was browser configurable, ultra low power, Ethernet enabled and could be easily adapted to virtually any data capture and control application. IO Anywhere devices provide affordable internet/intranet connectivity to a vast array of both legacy devices and leading edge stand alone equipment. Utilising the latest in CPLD technology and integrating Ethernet enabled microprocessor core modules produces a completely configurable platform for a broad range of applications.
 Debian
Debian
Debian Weekly News highlighted Nori Heikkinen's howto document that describes in detail how to install Debian on a Dell Inspiron 8000 notebook. This includes configuration for the video card, an external mouse and hints on rescuing the system from the boot CD. She would appreciate any comments, suggestions and improvements people have about it.
Also from DWN comes the info that Adam Powell has relocated documentation on Debian Beowulf resources to the Debian Wiki.
IBM DeveloperWorks guide to creating Debian Linux packages.
 Gentoo
Gentoo
A Gentoo Linux fork has been announced. Zach Welch annouced the fork of Gentoo Linux in a message to the gentoo-dev mailing list, the new project is to be called Zynot. Linux Weekly News have a good discussion of this development which includes links to background material.
 Mandrake
Mandrake
MandrakeSoft CEO François Bancilhon has issued An open letter giving an update on Mandrake's status, and the progress that has been made since the company applied for Chapter 11 protection at the beginning of the year.
 Red Hat
Red Hat
The Register recently reported on Red Hat's decision to discontinue retail sales and to refocus the business's interests.
 SCO
SCO
SCO has announced that it has terminated IBM's right to use or distribute AIX software, and files amended complaint against IBM, including a permanent injunction against IBM for destruction or return of all copies of UNIX System V Source Code and permanent cessation of AIX distribution The SCO Group calls itself "a leading provider of business software solutions".
 SuSE
SuSE
SuSE Linux has announced that the SuSE Linux Enterprise Server 8 has reportedly achieved the highest performance rating on any 32- or 64-bit Intel based server running the Linux operating system in the Oracle Applications Standard Benchmark (OASB), in a non clustered environment. Testing for the OASB was conducted on Oracle E-Business Suite version 11.5.6 and Oracle-9i Database Enterprise Edition, Release 2. The benchmark was run on an IBM eServer xSeries x440 system, based on Intel� Xeon MP processors at 2.0 Ghz, using SuSE Linux Enterprise Server 8, powered by UnitedLinux. For more information on the Oracle Application Standard Benchmark, please visit, http://www.oracle.com/apps_benchmark/
SuSE Linux has also announced that HP will resell and support SuSE Linux Enterprise Server 8, powered by UnitedLinux, on industry-standard HP ProLiant servers and HP's Itanium-based servers.
SuSE Linux has announced that it has been chosen by Cray Inc. to drive key aspects of the U.S. Department of Energy's new massively parallel processing (MPP) supercomputer called Red Storm at Sandia National Laboratories, California, which, when completed, will be the fastest supercomputer in the US. Red Storm is expected to become operational in late 2004 timeframe and will use AMD Opteron processors. featuring HyperTransport technology in conjunction with Red Storm's high-bandwidth, low-latency internal switching architecture. The Sandia National Laboratories Red Storm supercomputer will be used for computer simulations of the U.S. nuclear stockpile and other applications.
 An Gramadóir
An Gramadóir
Kevin Scannell has written an Irish Language grammar checker that works under Linux/Unix, etc. It has been built upon the same database used by Kevin to create wordlists for ispell and Gaelspell, and is distributed under the terms of the GPL.
 IBM Unveils Linux-Based Employee Workplace Portal
Solution for Medium Businesses
IBM Unveils Linux-Based Employee Workplace Portal
Solution for Medium Businesses
IBM has announced the IBM Integrated Platform Express for Employee Workplace, a new Linux-based server portal solution that is intended to enhance the productivity of midsized companies with busy office environments. Organizations with this solution will improve employee effectiveness by allowing them to access, communicate, customize and manage all their business information and collaborative workplace applications, all via a single Web browser.
 Softbank Uway of Korea Selects Linux
Softbank Uway of Korea Selects Linux
Korea-based Softbank Uway recently replaced 45 database and Web servers from HP and Sun with a single new IBM z990 "T-Rex" mainframe. The company plans to move to Linux running in partition on the z990 with IBM's z/VM virtualization technology and, in so doing, dramatically simplify its systems management and reduce software costs.
 SIMPL Announces v2.2.0 with Python Extensions
SIMPL Announces v2.2.0 with Python Extensions
The SIMPL open source project has just released v2.2.0. Although the original SIMPL library was written in C, over the years an impressive array of language extensions have been added including Tcl/Tk, JAVA, C++ and now Python. The project claims that SIMPL messaging has now become almost language agnostic. SIMPL was originally developed to run on Linux. It has since been ported to AIX and Mac OSX. It also interfaces with QNX.
SIMPL has always been designed to be such that code is insulated from details of network messaging. There are surrogates for TCP/IP sockets with additional UDP, raw ethernet and raw serial surrogates in development. With the recent release of the IO Anywhere box the project comes very close to having "SIMPL in silicon" and certainly have a very capable SIMPL enabled appliance.
Mick is LG's News Bytes Editor.
![[Picture]](../gx/2002/tagbio/conry.jpg) Born some time ago in Ireland, Michael is currently working on
a PhD thesis in the Department of Mechanical Engineering, University
College Dublin. The topic of this work is the use of Lamb waves in
nondestructive testing. GNU/Linux has been very useful in this work, and
Michael has a strong interest in applying free software solutions to
other problems in engineering. When his thesis is completed, Michael
plans to take a long walk.
Born some time ago in Ireland, Michael is currently working on
a PhD thesis in the Department of Mechanical Engineering, University
College Dublin. The topic of this work is the use of Lamb waves in
nondestructive testing. GNU/Linux has been very useful in this work, and
Michael has a strong interest in applying free software solutions to
other problems in engineering. When his thesis is completed, Michael
plans to take a long walk.
|
...making Linux just a little more fun! |
By Javier Malonda |
The Ecol comic strip is written for escomposlinux.org (ECOL), the web site tha t supports, es.comp.os.linux, the Spanish USENET newsgroup for Linux. The strips are drawn in Spanish and then translated to English by the author.
These images are scaled down to minimize horizontal scrolling. To see a panel in all its clarity, click on it.
All Ecol cartoons are at tira.escomposlinux.org (Spanish), comic.escomposlinux.org (English) and http://tira.puntbarra.com/ (Catalan). The Catalan version is translated by the people who run the site; only a few episodes are currently available.
These cartoons are copyright Javier Malonda. They may be copied, linked or distributed by any means. However, you may not distribute modifications. If you link to a cartoon, please notify Javier, who would appreciate hearing from you.
|
...making Linux just a little more fun! |
By David Lechnyr |
When installing software, many people are confused. "Should I install in /usr/sbin? /usr/local? /usr/local/packagename?" The additional belief in "one right way" to install software adds to this confusion. In this short article, it is hoped that some of these confusions can be illuminated so that the user can make an informed choice.
The Filesystem Hierarchy Standard (FHS) is a reference on how to manage a Unix filesystem or directory hierarchy. Unfortunately many people assume it is a standard and/or tutorial, which is opposite of their mission statement. The FHS is a subset of the Linux Standard Base (LSB), which promotes a set of standards to increase compatibility among Linux distributions and enable software applications to run on any compliant system. However, whether intentional or not, these standards tend to be adopted by Linux distribution vendors rather than by software package maintainers.
Take, for example, Samba. The default installation directory for Samba is
/usr/local/samba. Many people complain that this sort of
thing violates the FHS. What they fail to realize is what we have stated above: The adoption of the FHS seems to be encouraged
in Linux distribution vendors rather than with Linux software maintainers. It is somewhat uncertain as to why this is and
whether it is intentional or not. Regardless, the effect ends up being not unlike a dog barking at its own tail -- the audience
is complaining about one thing when it was never the focus of attention in the first place. Whether intentional or not is a
moot point at best; this is how it currently is playing out.
The installation location for many software packages is traditionally steeped in historical precedence. Many software maintainers assert that they install in /usr/local/packagename not out of any method
or philosophy, but rather because "we've always done it that way". And in the world of well-tuned software, if it
isn't broke, it isn't fixed.
Not that I disagree. Historical precedence is an important aspect. Alternately, the FHS has some excellent ideas towards standardizing the location of installed files and directories. However, it is just simply that: a philosophy without encouragement of compliance. In neither focusing or encouraging their philosophy on software package maintainers nor Linux distribution vendors, the reaction to the FHS from the Internet community seems to reflexively be from the distribution vendor. In truth, this is part of the problem.
Focus on FHS compliance, whether intentional or not, should be placed on the software developers. This will clear up some of the more traditional problems. For example:
Example 1: Before the advent of the FHS
A user installs RedHat Linux. After some time, she decides to upgrade one of the software packages by hand. No file location conflicts exist, as the installation location under RedHat Linux for each software program is determined by the software vendor. Packages installed in /usr/local/packagename will be replaced by files in the same location.
Example 2: After the advent of the FHS
A user installs RedHat Linux. After some time, he decides to upgrade one of the software packages by hand. However, his software package is installed in /usr/bin and /usr/sbin along with variable data files in /var/lib/packagename. The upgraded software package he just downloaded installs everything by default into /usr/local/packagename. Being an average Linux user, he is somewhat perplexed by what conflicts this may introduce into his system and is unsure how to proceed.
Personally, I think we're focusing on the wrong angle for FHS-compliance. An alternate future reality, which would be much better, would be:
Example 3: In the future
A user installs RedHat Linux. After some time, she decides to upgrade one of the software packages by hand. No file location conflicts exist, as the installation location under RedHat Linux for each software program is determined by the FHS-compliant software vendor (and not by RedHat). RedHat itself makes no modifications to the installation defaults for each software package. Packages installed in on the system, whether by RPM or compiled by hand, will replaced files on the system in the exact same location.
With the upcoming release of version 2.3 of the FHS, it becomes even more important that we focus on the right issues. If we are to succeed at minimizing confusion in the world of installable Linux software, we need to not only focus on our philosophy and method but also on the correct audience. Hopefully, this article has helped make you more aware of the issues at hand.
Some of the many distributions that attempt to maintain LFH-compliance include:
![[BIO]](../gx/2002/note.png) David Lechnyr is a Network Administrator for the Human
Resources department at the University of Oregon. He holds a Master's Degree in Social Work along with his MCSE+I, CNE, and
CCNA certifications. He has been working with Linux for the past seven years, with an emphasis on systems security, network
troubleshooting, and PHP/MySQL integration. He is also the author of the Unofficial Samba HOWTO and the Linux+Apache+MySQL+PHP HOWTO.
David Lechnyr is a Network Administrator for the Human
Resources department at the University of Oregon. He holds a Master's Degree in Social Work along with his MCSE+I, CNE, and
CCNA certifications. He has been working with Linux for the past seven years, with an emphasis on systems security, network
troubleshooting, and PHP/MySQL integration. He is also the author of the Unofficial Samba HOWTO and the Linux+Apache+MySQL+PHP HOWTO.
|
...making Linux just a little more fun! |
By Yufei Yuan |
Many of us gnu/linux users have had such a terrible experience. When you login and type the sweet startx as usual, you only receive scrolling lines of error messages. One copy of the error message is usually stored in /var/log/XFree86.0.log. If you can access the log file, you will notice the last lines of the file may look like this:
Could not init font path element unix/:7100, removing from list! Fatal server error: could not open default font 'fixed'
I have to admit that I was in panic when I saw this message in the first several times. As an intermediate user of linux system, I was not so comfortable using text console for modem dialup and surfing with lynx. So I had to spend a lot of time on another box and use Google to search for help on web. It was amazing that so many people like me have this exact terrible experience and those replies in web forums and mailing lists generally offer more sympathy than real help. Using our common sense and some research, most of us can figure out this failure has something to do with X font server.
After having done a little more research, now I believe that this failure may not be so serious as it looks. Please follow me by doing the steps below, in most of the cases you will get your X windows starting up again.
Note: The following examples run on my Red Hat box. But I believe they are general enough to be used for other distributions.
1. Check if the X font server is running.
Some people like me tend to suspect it is caused by bugs in the X font server, but it turned out that X font server is quite robust. We can run the xfs script under /etc/init.d to see if the font server is running.
[root@localhost /root]# /etc/init.d/xfs status xfs (pid 1385) is running...
In some cases, the only reason for the failure is that the font server is dead. So, you need to restart font server like this:
[root@localhost /root]# /etc/init.d/xfs start Starting xfs: [ OK ]
Well, my learned lesson is don't take this '[OK]' for granted. You have to check the status again to see if it is running. If it does run, you can try startx to see if you can start X windows. If you still cannot start X server when the font server runs, it means you are having more serious trouble. You need to waste a little more time reading on the following steps.
Note: In a weird case, my root partition was fully filled by two huge log files occupying more than 2 GB. The font server dies when it cannot write to /tmp. So the simple solution was finding the huge files and deleting them.
2. Check if the font 'fixed' is accessible.
Now it is time to ensure that the font 'fixed' is accessible. First, we can use command fslsfonts to see if font 'fixed' exists in the search path:
[root@localhost alex]# fslsfonts -server unix/:7100 -ll -fn fixed DIR MIN MAX EXIST DFLT ASC DESC NAME --> 0 255 some 0 11 2 fixed FONTNAME_REGISTRY FOUNDRY Misc FAMILY_NAME Fixed WEIGHT_NAME Medium SLANT R SETWIDTH_NAME SemiCondensed ADD_STYLE_NAME PIXEL_SIZE 13 POINT_SIZE 120 RESOLUTION_X 75 RESOLUTION_Y 75 SPACING C AVERAGE_WIDTH 60 CHARSET_REGISTRY ISO8859 CHARSET_ENCODING 1 COPYRIGHT Public domain font. Share and enjoy. CAP_HEIGHT 9 X_HEIGHT 6 FONT -Misc-Fixed-Medium-R-SemiCondensed--13-120-75-75-C-60-ISO8859-1 WEIGHT 10 RESOLUTION 103 QUAD_WIDTH 6
This is the normal output when 'fixed' is available. Here, we can see that 'fixed' is actually an alias for the font '-Misc-Fixed-Medium-R-SemiCondensed--13-120-75-75-C-60-ISO8859-1'. If there is no font 'fixed', we first need to gain knowledge of the search path for fonts. We can use command chkfontpath to look at those paths:
[root@localhost alex]# /usr/sbin/chkfontpath Current directories in font path: 1: /usr/X11R6/lib/X11/fonts/misc:unscaled 2: /usr/X11R6/lib/X11/fonts/75dpi:unscaled 3: /usr/X11R6/lib/X11/fonts/100dpi:unscaled 4: /usr/X11R6/lib/X11/fonts/misc 5: /usr/X11R6/lib/X11/fonts/Type1 6: /usr/X11R6/lib/X11/fonts/Speedo 7: /usr/X11R6/lib/X11/fonts/CID 8: /usr/X11R6/lib/X11/fonts/75dpi 9: /usr/X11R6/lib/X11/fonts/100dpi 10: /usr/share/fonts/default/Type1 11: /usr/share/fonts/default/TrueType 12: /usr/share/fonts/ja/TrueType 13: /usr/X11R6/lib/X11/fonts/latin2/100dpi:unscaled 14: /usr/X11R6/lib/X11/fonts/latin2/100dpi 15: /usr/share/fonts/ISO8859-7/misc:unscaled 16: /usr/share/fonts/ISO8859-7/75dpi:unscaled 17: /usr/share/fonts/ISO8859-7/100dpi:unscaled 18: /usr/share/fonts/ISO8859-7/misc 19: /usr/share/fonts/ISO8859-7/Type1 20: /usr/share/fonts/ISO8859-7/75dpi 21: /usr/share/fonts/ISO8859-7/100dpi 22: /usr/share/fonts/ISO8859-9/misc:unscaled 23: /usr/share/fonts/ISO8859-9/100dpi:unscaled 24: /usr/share/fonts/ISO8859-9/misc 25: /usr/share/fonts/ISO8859-9/100dpi 26: /usr/share/fonts/KOI8-R/100dpi:unscaled 27: /usr/share/fonts/KOI8-R/100dpi 28: /usr/share/fonts/zh_CN/TrueType 29: /usr/share/fonts/zh_TW/TrueType 30: /usr/share/AbiSuite/fonts
These are the font paths on my box. It shows that xfs looks into these paths seeking a specific font when it is required. There are two types of important files: fonts.dir in each of these paths, and fonts.alias in some of the paths. For example, let's go to /usr/X11R6/lib/X11/fonts/100dpi, and open the files. The files look like this:
[fonts.dir] 775 UTI___14.pcf.gz -adobe-utopia-regular-i-normal--19-140-100-100-p-104-iso10646-1 UTBI__14.pcf.gz -adobe-utopia-bold-i-normal--19-140-100-100-p-109-iso10646-1 UTI___12.pcf.gz -adobe-utopia-regular-i-normal--17-120-100-100-p-89-iso10646-1 UTI___24.pcf.gz -adobe-utopia-regular-i-normal--33-240-100-100-p-179-iso10646-1 courO08.pcf.gz -adobe-courier-medium-o-normal--11-80-100-100-m-60-iso10646-1 UTBI__12.pcf.gz -adobe-utopia-bold-i-normal--17-120-100-100-p-93-iso10646-1 ...
The first line specifies the number of fonts under current directory. Following lines map file names to font names.
[fonts.alias] lucidasans-bolditalic-8 -b&h-lucida-bold-i-normal-sans-11-80-100-100-p-69-iso8859-1 lucidasans-bolditalic-10 -b&h-lucida-bold-i-normal-sans-14-100-100-100-p-90-iso8859-1 lucidasans-bolditalic-12 -b&h-lucida-bold-i-normal-sans-17-120-100-100-p-108-iso8859-1 lucidasans-bolditalic-14 -b&h-lucida-bold-i-normal-sans-20-140-100-100-p-127-iso8859-1 lucidasans-bolditalic-18 -b&h-lucida-bold-i-normal-sans-25-180-100-100-p-159-iso8859-1 lucidasans-bolditalic-24 -b&h-lucida-bold-i-normal-sans-34-240-100-100-p-215-iso8859-1 ...
This file maps font alias to font names. So it is clear that once font 'fixed' is needed, the font server search fonts.alias in each font path for a match. If the match exists, the corresponding font file is specified in fonts.dir. If no match exists, which is a rare situation, the X server cannot start and we need to rebuild the font lists. The rebuilding process will generate new fonts.dir and fonts.alias files.
3. Rebuild font list.
Font list can be rebuilt using the script file xfs under /etc/init.d. Following is an excerpt of the script:
...
buildfontlist() {
pushd . &> /dev/null
for d in $(/usr/sbin/chkfontpath --list | cut -f 2 -d ':') ;do
if [ -d "$d" ]; then
cd $d
# Check if we need to rerun mkfontdir
NEEDED=no
if ! [ -e fonts.dir ]; then
NEEDED=yes
elif [ "$(find . -type f -cnewer fonts.dir 2>/dev/null)" != "" ];then
NEEDED=yes
fi
if [ "$NEEDED" = "yes" ]; then
...
}
...
start() {
if [ -L /usr/X11R6/bin/X ]; then
echo -n $"Starting $prog: "
[ -x /usr/sbin/chkfontpath ] && buildfontlist
rm -fr /tmp/.font-unix
daemon xfs -droppriv -daemon
ret=$?
[ $ret -eq 0 ] && touch /var/lock/subsys/xfs
echo
return $ret
fi
}
...
For readers not familiar with shell programming, this excerpt means that each time xfs script is run, it will check whether there is a fonts.dir file in each listed font path. If fonts.dir is missing in a path, font list needs to be rebuilt. If a fonts.dir does exist for each path, it will check if the status of any file in the font directory is changed after the last change of fonts.dir. If this is true, the font list also needs to be rebuilt.
For newbies not interested in learning shell programming, we play a small trick in the subroutine buildfontlist(). We can set "NEEDED=yes" in the first instance to force the rebuilding of font list.
4. Fonts really missing?
If all steps above fail. My last suggestion is to check if the font file is really removed by some processes. Then you need to reinstall the font.
![[BIO]](../gx/2002/note.png) Yufei is a graduate student in the University of Alberta. He uses GNU/linux for work and for fun. He develops image and video compression algorithms on GNU/Linux for his research project. His RH9 box@home has a Conexant HSF winmodem, which works pretty well for browsing the Web and listening to streamed audio.
Yufei is a graduate student in the University of Alberta. He uses GNU/linux for work and for fun. He develops image and video compression algorithms on GNU/Linux for his research project. His RH9 box@home has a Conexant HSF winmodem, which works pretty well for browsing the Web and listening to streamed audio.
|
...making Linux just a little more fun! |
By Dean Wilson |
"Its only running a single service, we're fully patched and it has a local firewall that denies by default."
One of the basic premises of computer security is that it's almost impossible to fully secure any machine to which an attacker has physical access. While we cannot cover all eventualities, we can make some simple changes to catch any use of the more blatant avenues of abuse. In this document we will cover how to stop unauthorised people from casually rebooting your machines.
Anyone who walks up to a keyboard connected to a Linux machine can press Control-Alt-Delete to reboot it without entering a username or a password. Even Windows machines require a valid login (either the current user or one with Administrator privileges) before you can reboot a running machine like this if it has a locked screen. This does not even have to be an issue of malice, it is not uncommon for people familiar with Windows NT or Windows 2000 to use Control-Alt-Delete in an X-Windows session expecting to be shown a screen to lock the workstation, or open the task manager and instead seeing the dreaded "The system is going down for reboot NOW!" message as their work vanishes along with the systems uptime.
In many Linux distributions the key combination of Control-Alt-Delete (Which is often referred to as ctrl-alt-del or "the 3 finger salute") is pre-configured to reboot the machine. While this may be acceptable for a single user desktop at home it is an unnecessary risk for office workstations or even servers because of one important fact, it requires no authentication to perform.
To prevent this destructive behavour we are going catch Control-Alt-Delete's and disable this "feature" by replacing the default action with a script of our own. We will also add auditing in order to catch and log any attempts to reboot. To do this we will add a single shell script to the system, make a change to the '/etc/inittab' configuration file so our own handler gets called and then add a little log rotation (If you run 'logrotate') to keep everything shipshape.
The bash shell script that does most of the actual work is called 'audit_cad.sh' and can be found here. It can be invoked in two ways. The first way is to call it is with the '-c' argument. In this mode the script will check that all of its external dependencies are both present and executable. This is the best way to ensure that your system satisfies all the prerequisites.
If any of the tests fail then an error will be printed containing the name of the suspect binary and the script will carry on until it has finished checking them all. If any of the checks fail, when the script finishes executing a exit code of '1' will be returned. The external binaries we depend on are:
Of these the only one that may need manual editing is basename which often varies between the '/usr/bin' and '/bin' directories. Typically you will run the script in check mode when you first install it to ensure that it will run correctly and nothing is missing. As this script is run as root it is a good idea to ensure that the permissions are as tight as possible with only the super user having any access to the file. Ideally they should be set to -rwx------, you can do this with the following command; 'chmod 0700 audit_cad.sh'.
The second way to call it is without arguments, when run in this fashion it logs an entry to both 'syslog' (with a user specified facility and level) and an external file, which defaults to '/var/log/shutattempt'. This is how it will be executed to audit Control-Alt-Delete's.
For the purposes of this document we call the script 'audit_cad.sh' and it is located in '/usr/local/sbin/'. To change either of these settings or any of the other ones just open the script in your editor of choice and scroll along. All the configuration options are commented.
Now we have the script in place we are going to edit the default handler for Ctrl-Alt-Delete in the '/etc/inittab' file. The line we want instructs 'init' to listen for Control-Alt-Delete events and tells it to execute a specific command when it receives one. In most distributions the id will be 'ca' and the actual entry will look similar to "ca:12345:ctrlaltdel:/sbin/shutdown -t1 -a -r now" The important section of this line is the last field which begins '/sbin/shutdown', to change the systems behaviour you can edit the current command and point it to our 'audit_cad.sh' script. If you have been following along with the examples the full path will be '/usr/local/sbin/audit_cad.sh'
Once you have made this change you need to tell the 'init' process that 'inittab' has changed. The easiest way of doing this is to run 'telinit q' which causes 'init' to reread its configuration file without restarting
Now we are in a position to test our changes, before you do this i recommend closing down anything that is not essential to the system such as GUI's and editing sessions, if we have made a mistake while following the examples the system is about to reboot and its better to be safe than annoyed at the author! When you are ready press Ctrl-Alt-Delete and nothing at all should happen.
If your system is still up at this point then check both the syslog file (typically this is '/var/log/messages' or '/var/log/syslog') and the external log file we specified in the 'audit_cad.sh' file to ensure that the logging was successful. If your system has rebooted then check each step and try again.
Once you have this working it's worth going the final mile and adding some automated log processing. This can vary from setting up 'SWATCH' or 'logwatch' to send you automated alerts to adding log rotation to keep the file sizes down. A simple example if you have 'logrotate' running on your machine (Both recent Redhat and Debian distributions do) is given below and can also be found here.
daily
rotate 7
compress
delaycompress
/var/log/shutattempt {
nomail
notifempty
missingok
create 0600 root root
}
To add this to 'logrotate''s processing list just add a file called audit_cad to your 'logrotate' directory, which is often located at '/etc/logrotate.d' with the above snippet or another similar one as contents and you no longer have to worry about it eating up disk space.
While this technique will successfully log any attempts to reboot the machine there are a couple of points worth noting. The first is accountability, it is not possible using this script alone to determine who actually tried to take the machine over. This is because no authentication information is available for logging, 'init', the program that actually handles the Ctrl-Alt-Delete, runs as root so any attempts to capture the invoking username will return 'root'.
By making some minor changes to 'audit_cad.sh' it would be possible to capture the output of w or who to the logs but this information isn't as useful as you may think in this situation, these commands only track the valid users that have supplied credentials to logon, something that someone who just walks upto your keyboard and presses Control-Alt-Delete does not need to supply and so the person who actually tried is the only one not logged!
The second point to consider is how obvious to make this script. If you want to be sneaky and obscure its presence you can call it 'shutdown' and save it in a non-standard location.
For further information on the format and purpose of 'inittab' please see 'man 5 inittab' and for a full list of the options 'telinit' supports please read 'man 8 telnint'. If you are unfamiliar with 'logrotate' then its manpage is a good starting point 'man 8 logrotate'.
![[BIO]](../gx/2002/note.png) Dean Wilson is (this week) a systems administrator and occasional
updater to his pages at www.unixdaemon.net
Dean Wilson is (this week) a systems administrator and occasional
updater to his pages at www.unixdaemon.net
|
...making Linux just a little more fun! |
By Ivan Pesin |
The main purpose of this document is to describe and explain steps you need to perform to setup a Linux authentication via Novell e-Directory.
Novell e-Directory is a Novell implementation of an access protocol to X.500-based directory services. Another implementation of this protocol is known as LDAP, Lightweight Directory Access Protocol. LDAP is defined in RFC2251 "The Lightweight Directory Access Protocol (v3)".
A directory is similar to a database, but tends to contain more descriptive,
attribute-based information. The information in a directory is generally read
much more often than it is written. Directories are tuned to give quick-response
to high-volume lookup or search operations. They may have the ability to replicate
information widely in order to increase availability and reliability, while
reducing response time. When directory information is replicated, temporary
inconsistencies between the replicas may be OK, as long as they get in sync
eventually.
The following is a quick start guide to setup Linux authentication and account information fetching via Novell e-Directory.
It is meant to walk you through the basic steps needed to setup authentication procedure. It should be used in conjunction with the other chapters of this document, manual pages, and other materials provided with the default distribution.
If you intend to work with authentication via Novell e-Directory seriously, you should review this entire document before attempting to setup the software.
To setup Novell e-Directory authentication you have to perform following steps:
/etc/ldap.conf configuration file
First of all you have to setup ldap.conf file, which is usually situated in /etc directory. Let's take a look on it:
# your Novell e-Directory server IP address
server 192.168.0.1
# base context
base ou=london,o=acme
# special user, which is used only for NDS tree browsing
# and has appropriate rights
binddn cn=ndsbrowser,ou=london,o=acme
# users password
bindpw ndspass
# enable ssl encryption
ssl yes
# password mode NDS pam_password nds
# special attribute mapping
nss_map_attribute userPassword authPassword
# NDS search scope
scope subb. PAM system configuration
Now we have to change configuration for PAM (pluggable authentication modules) system. For that in RedHat 7.3 we have to change file /etc/pam.d/system-auth. Here it goes:
#%PAM-1.0
auth required /lib/security/pam_env.so
auth sufficient /lib/security/pam_unix.so likeauth nullok
auth sufficient /lib/security/pam_ldap.so try_first_pass
auth required /lib/security/pam_deny.so
account sufficient /lib/security/pam_unix.so
account [default=bad success=ok user_unknown=ignore service_err=ignore system_err=ignore] /lib/security/pam_ldap.so
password required /lib/security/pam_cracklib.so retry=3 type=
password sufficient /lib/security/pam_unix.so nullok use_authtok md5 shadow
password sufficient /lib/security/pam_ldap.so use_authtok
password required /lib/security/pam_deny.so
session required /lib/security/pam_limits.so
session required /lib/security/pam_unix.so
session required /lib/security/pam_mkhomedir.so skel=/etc/skel/ umask=0077
session optional /lib/security/pam_ldap.soSo, we've setup password authentication. Let's go to the next section.
c. Name service switch configuration
Now we've to setup linux account data fetching from Novell e-Directory. For that we have to edit file /etc/nsswitch.conf. Simply check if the lines, which starts from "passwd:", "shadow:" and "group:" contains word "ldap". If not -- you've to add it. On my PC it looks like:
# Look for passwd in local files then in ldap
passwd: files ldap
# Look for shadow in local files then in ldap
shadow: files ldap
# Look for group in local files then in ldap
group: files ldapd. SSL security configuration
Last step we have to perform on Linux box is to setup secure connection to the Novell server. To do it download file RootCert.der from SYS: volume of the Novell server and save it into cert directory /usr/share/ssl/certs. Convert the Novell root certificate using the command:
openssl x509 -in /usr/share/ssl/certs/RootCert.der -inform DER -out \
/usr/share/ssl/certs/RootCert.pem -outform PEMIn the openssl.cnf (on RedHat 7.3 in /usr/share/ssl directory) file set the "value certificate" to point to the RootCert.pem (certificate being the CA certificate) and "my private key" to be the same certificate.
Okay, we've done all things on Linux. Now it's time to switch to Novell server. There are some things that should be done. All things we're going to do can be done via ConsoleOne tool.
e. Novell side configuration
First of all we've to make some changes into NDS <–> LDAP mapping scheme. To do that, open your base context and find "LDAP Group" item. Open properties of this object. In the "General" tab check "Allow Clear Text Passwords" box (it’s for testing purposes).
Now open "Attribute Map" tab. Click "Add" button and add following mappings:
LDAP Attribute NDS Attribute loginShell loginShell uidNumber uidNumber gidNumber gidNumber Close "LDAP Group" properties dialog.
Second step is to setup user account properly. For that right-click on appropriate user and select properties. Open "UNIX Profile" tab and enter the account data:
Here is a short legend:
uid (User ID) - should be unique for all users gid (Group ID) - group number login shell - user’s login shell comment - any comment, full name is an example home directory - user’s home directory.
In this part of the document we will go deeply into background of the Linux authentication via Novell e-Directory process. It mainly consists of two logical parts: password authentication and account data fetching. Understanding of that processes will allow you to setup authentication on other not described linux distributions.
Password authentication via ldap is implemented with pam_ldap module. It has to be installed if you wish to organize password authentication via ldap. For RedHat Linux 7.3 is available nss_ldap RPM package within distribution. It contains all tools, modules and libraries needed as for password authentication, so for linux account data fetching.
Software needed for LDAP authentication is public domain software maintained
by PADL Software Company in Melbourne, Australia. Company runs three Internet
mailing lists that allow users of their software to support each other: nssldap@padl.com,
pamldap@padl.com, and ldap-nis@padl.com. If you wish to subscribe to any of
these mailing lists, send an e-mail to majordomo@padl .com with "subscribe
listname" in the message body.
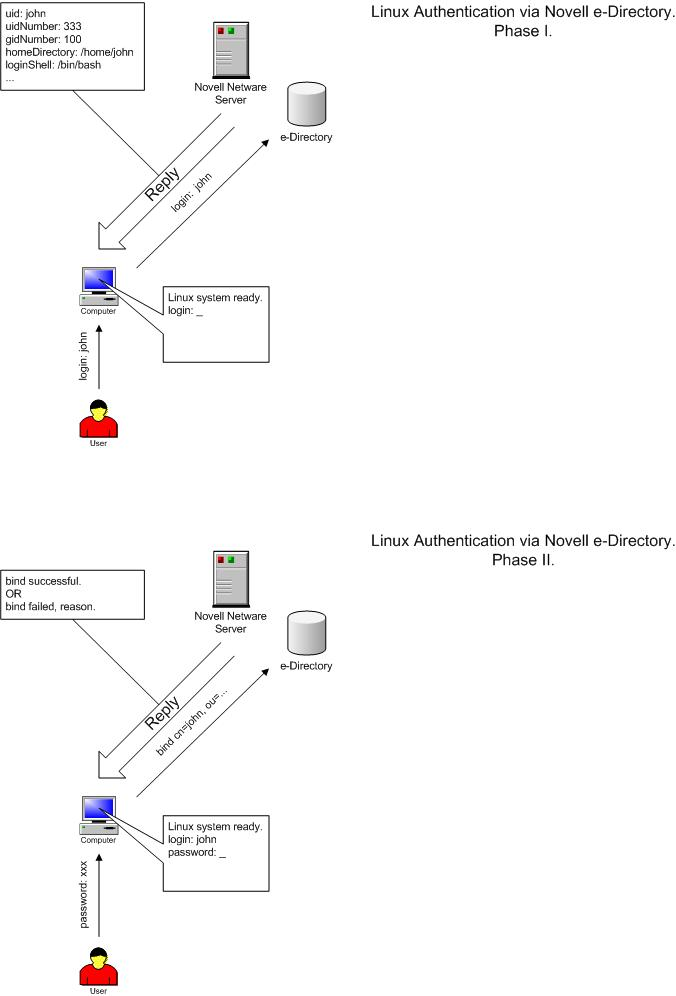
a. PAM_LDAP and NSS_LDAP.
The ldap.conf file is used to configure LDAP-specific information for the pam_ldap modules and libnss_ldap library. The following list represents minimum required records in this file to provide SSL-encrypted communication with Novell e-Directory server:
host <ip address or hostname of eDirectory server>
base <container at which to begin searching for information in eDirectory>
scope sub - specifies a subtree search.
ssl on - turn on SSL transport encryption
We need to authenticate as a specific user when retrieving user information because of access to some user information not available in the context of anonymous bind. For that the following parameters must be set :
binddn <full LDAP DN of user object to authenticate as>
bindpw <password of the above user>
The following listing shows the example of ldap.conf file :
server 192.168.0.1
base ou=london,o=acme
binddn cn=ndsbrowser,ou=london,o=acme
bindpw ndspass
ssl yes
pam_password nds
nss_map_attribute userPassword authPassword
scope subb. PAM System.
Editing a specific file configures PAM. In RedHat Linux 7.3 you will need to edit file called system-auth situated in the /etc/pam.d directory. An entry in this file defines authentication systems (traditional UNIX authentication, LDAP, smart cards, and so on) which will be used for authentication. Modules can be stacked. Depending on how the modules are stacked and configured, multiple services may be used.
Each entry in the configuration file has three required fields and an optional field.
Linux-PAM separates the tasks of authentication into four independent management groups: account management; authentication management; password management; and session management.
Simply put, these groups take care of different aspects of a typical user's request for a restricted service:
account - provide account verification types of service: has the user's password expired?; is this user permitted access to the requested service?
authentication - establish the user is who they claim to be. Typically this is via some challenge-response request that the user must satisfy: if you are who you claim to be please enter your password. Not all authentications are of this type, there exist hardware based authentication schemes (such as the use of smart-cards and biometric devices), with suitable modules, these may be substituted seamlessly for more standard approaches to authentication - such is the flexibility of Linux-PAM.
password - this group's responsibility is the task of updating authentication mechanisms. Typically, such services are strongly coupled to those of the auth group. Some authentication mechanisms lend themselves well to being updated with such a function. Standard UN*X password-based access is the obvious example: please enter a replacement password.
session - this group of tasks cover things that should be done prior to a service being given and after it is withdrawn. Such tasks include the maintenance of audit trails and the mounting of the user's home directory. The session management group is important as it provides both an opening and closing hook for modules to affect the services available to a user.
When a Linux-PAM aware privilege granting application is started, it activates its attachment to the PAM-API. This activation performs a number of tasks, the most important being the reading of the configuration file(s): /etc/pam.conf. Alternatively, this may be the contents of the /etc/pam.d/ directory.
These files list the PAMs that will do the authentication tasks required by this service, and the appropriate behavior of the PAM-API in the event that individual PAMs fail.
The syntax of the /etc/pam.conf configuration file is as follows. The file is made up of a list of rules, each rule is typically placed on a single line, but may be extended with an escaped end of line: `\<LF>'. Comments are preceded with `#' marks and extend to the next end of line.
The format of each rule is a space separated collection of tokens, the first three being case-insensitive:
service type control module-path module-arguments
The syntax of files contained in the /etc/pam.d/ directory, are identical except for the absence of any service field. In this case, the service is the name of the file in the /etc/pam.d/ directory. This filename must be in lower case.
An important feature of Linux-PAM, is that a number of rules may be stacked to combine the services of a number of PAMs for a given authentication task.
The service is typically the familiar name of the corresponding application: login and su are good examples. The service-name, other, is reserved for giving default rules. Only lines that mention the current service (or in the absence of such, the other entries) will be associated with the given service-application.
The type is the management group that the rule corresponds to. It is used to specify which of the management groups the subsequent module is to be associated with. Valid entries are: account; auth; password; and session. The meaning of each of these tokens was explained above.
The third field, control, indicates the behavior of the PAM-API should the module fail to succeed in its authentication task. There are two types of syntax for this control field: the simple one has a single simple keyword; the more complicated one involves a square-bracketed selection of value=action pairs.
For the simple (historical) syntax valid control values are: requisite - failure of such a PAM results in the immediate termination of the authentication process; required - failure of such a PAM will ultimately lead to the PAM-API returning failure but only after the remaining stacked modules (for this service and type) have been invoked; sufficient - success of such a module is enough to satisfy the authentication requirements of the stack of modules (if a prior required module has failed the success of this one is ignored); optional - the success or failure of this module is only important if it is the only module in the stack associated with this service+type.
For the more complicated syntax valid control values have the following form:
[value1=action1value2=action2...]
Where valueN corresponds to the return code from the function invoked in the module for which the line is defined. The full list of PAM errors is available in /usr/include/security/_pam_types.h . For details refer to your local system documentation.
module-path - this is either the full filename of the PAM to be used by the application (it begins with a '/'), or a relative pathname from the default module location: /lib/security/.
module-arguments - these are a space separated list of tokens that can be used to modify the specific behavior of the given PAM. Such argu ments will be documented for each individual module.
The following listing shows a sample pam.conf file set up NDS authentication for all services in Red Hat Linux 7.3 . File "system-auth" in this distribution is included in each service module. Shown example provides authentications via LDAP, as well as traditional UNIX authentication if LDAP authentication fails. The file is also set up to include account authorization and password
The file is also set up to include account authorization and password management via LDAP and then files if the LDAP module fails.
#%PAM-1.0
auth required /lib/security/pam_env.so
auth sufficient /lib/security/pam_unix.so likeauth nullok
auth sufficient /lib/security/pam_ldap.so try_first_pass
auth required /lib/security/pam_deny.so
account sufficient /lib/security/pam_unix.so
account [default=bad success=ok user_unknown=ignore service_err=ignore system_err=ignore] /lib/security/pam_ldap.so
password required /lib/security/pam_cracklib.so retry=3 type=
password sufficient /lib/security/pam_unix.so nullok use_authtok md5 shadow
password sufficient /lib/security/pam_ldap.so use_authtok
password required /lib/security/pam_deny.so
session required /lib/security/pam_limits.so
session required /lib/security/pam_unix.so
session required /lib/security/pam_mkhomedir.so skel=/etc/skel/ umask=0077
session optional /lib/security/pam_ldap.soc. Name Switch Service.
The nsswitch.conf file, also located in the /etc directory, is used to configure which system will be used for shadow information (the shadow file) and password information (for authentication purposes). Each entry in the file consists of the name of the function and then a list of the modules to be referenced.The sample nsswitch.conf file listed below:
passwd: files ldap
shadow: files ldap
group: files ldapd. SSL Security.
In order to setup an SSL security, your Linux system must have a copy of the LDAP server's Trusted Root certificate. So you have to download file RootCert.der from SYS: volume of your Novell server to certs directory /usr/share/ssl/certs. Then you will need to convert the Novell root certificate using the command:
openssl x509 -in /usr/share/ssl/certs/RootCert.der -inform DER -out \
/usr/share/ssl/certs/RootCert.pem -outform PEMAfter converting set the value certificate to point to the RootCert.pem (certificate being the CA certificate) in the openssl.cnf (on RedHat Linux 7.3 system in /usr/share/ssl). Also set my private key to be the same certificate.
e. Novell e-Directory configuration
Now last steps of our battle for authentication are to setup Novell e-Directory server. We have to add some attributes in NDS <–> LDAP mapping scheme. For that you have to open in ConsoleOne your base context, find "LDAP Group" item, right-clicks with mouse and select "Properties...".
Now open "Attribute Map" tab. Find LDAP attributes with names "uidNumber", "gidNumber" and remove them, because there are broken mappings. Instead create new mappings, for that click "Add" button and add following mappings:
LDAP Attribute NDS Attribute loginShell loginShell uidNumber uidNumber gidNumber gidNumber The very last you should input apropriate values in "UNIX Profile" tab of each user. After that you can login linux box using your Novell credentials.
I want to notice some things. First: I've used in my investigation Novell Netware 6 with e-Directory 8.6.0 as server and my RedHat 7.3 linux box as client. I think that if you have some other version of software (newer) it should work also, may be with some evident changes. So, as far as I know if you'll use e-Directory 8.6.2 or higher there is fixed problem with attribute mappings, so you can omit appropriate section. Next: Unfortunelly we cannot setup fully secure authentication. At lease I don't see a way to do it. It is concerned with special user which has rights to browse NDS tree. File /etc/ldap.conf has to have +r for all users. So, everyone who has access to the linux box can see that password. It's not a really problem, while you gave rights only to read. But if you wish uses to set/change passwords directly from the command line by itselfs, you should give write rights to the special user. And here is a security hole. If you have a clue how to avoid such situation -- mail me ;-) Last but not least: product and company names mentioned herein may be the trademarks of their respective owners.
![[BIO]](../gx/2002/note.png) I work at N-iX Team of Newcomp Computersysteme GmbH
as senior network administrator. Currently I investigate communication of Linux
with other network server operation systems and support a lot of production
Linux servers. In the spare time I participate in Russian
Linux Gazette project, wich is official Russian-language mirror of LinuxGazette.
I work at N-iX Team of Newcomp Computersysteme GmbH
as senior network administrator. Currently I investigate communication of Linux
with other network server operation systems and support a lot of production
Linux servers. In the spare time I participate in Russian
Linux Gazette project, wich is official Russian-language mirror of LinuxGazette.
|
...making Linux just a little more fun! |
By Graham Jenkins |
This story actually started with a call from a user whilst I was strolling back to work through the sunshine one Friday lunchtime. The conversation went something like this:
"Hi Graham, we seem to be having a few problems in seeing the database for the ACME application. You want to take a look, please?"
"Sure, I'm ten minutes away from my desk, I'll call you back when I'm there. Everything on that server is mirrored; most likely scenario is that the archive logs are not being moved off to secondary storage. Should be able to resolve it in a few minutes."
And ten minutes later: "Guys, its going to take more that a few minutes. Something like a few hours, in fact. We seem to have lost disks from both sides of the mirrors!"
So what went wrong? The mirror pieces were on separate disks attached to separate controllers, there was no evidence of a major power spike or earth tremor. And we couldn't blame the night-time cleaning staff for pulling power cables so they could use their vacuum cleaners.
The answer is that we didn't lose both sides at once. We had actually lost one side a week earlier. My company has an excellent monitoring and alarm system for detecting such occurences, but we had forgotten to advise the alarm people that this server had moved from "build" status to "production" status. That's not something we are likely to do again!
A few weeks back, my home workstation experienced its second disk failure in six months. Sure, the disk got replaced again under warrantee. But I decided right then that I was going to mirror everything onto an additional disk.
Then I started thinking: "How would I know if a partition on one disk took itself off-line?" It's not like I can justify hooking my home workstation into my company's alarm system.
Did somebody say: "Check the messages file, read the 'root' email!"? Great theory guys. Trouble is, I have a partner whose idea of "messages" equates to a stack of Post-It notes, and who thinks that "email" means "Hotmail". And she has become a major user of my machine when I'm not around.
The solution here turned out to be a mechanism to flash the Scroll-Lock
light for a one second interval every ten seconds.
If a partition gets
unmirrored, the light gets left on. No extra hardware, dead easy to
understand.
 What we have here is a simple watchdog, which barks
periodically to show it is still alive, and barks continuously when
something goes wrong.
What we have here is a simple watchdog, which barks
periodically to show it is still alive, and barks continuously when
something goes wrong.
So how do you make the Scroll-Lock light flash? If you are using Xwindows, it's easy: 'xset led 3' turns it on, 'xset -led 3' turns it off. Even works if you have screen-lock running and/or your monitor powered off - provided you are logged in.
If nobody is logged in, or if you aren't using Xwindows, it isn't going to work. For that situation, you need to install something like the 'blinker' program which comes as part of the "morse2led" suite available at the node.to website.
Here's what you might see when you enter 'cat /proc/mdstat' on a machine which has a broken mirror:
Personalities : [raid1]
read_ahead 1024 sectors
md2 : active raid1 hda6[0] hdb6[1](F)
1959808 blocks [2/1] [U_]
md1 : active raid1 hda5[0] hdb5[1]
5863616 blocks [2/2] [UU]
md0 : active raid1 hda3[1] hdb3[0]
104320 blocks [2/2] [UU]
unused devices: <none>
And here's our program which detects when something is wrong (by searching
for an underscore in those lines containing 'blocks'), then activates the
scroll-lock light accordingly. It will run under most Bourne-like shells,
and has been extended to detect a couple of extra alarm conditions. You can
add to it as you see fit.
#!/bin/sh
# ledblink System monitor. Scroll-lock light will remain on if any faults.
# Graham Jenkins, IBM GSA, July 2003.
PATH=/sbin:/bin:/usr/bin:/usr/X11R6/bin:/usr/local/bin
On=1
while : ; do # Use 'blinker' if it works,
blinker -d `expr $On \* 1000` s 2>/dev/null ||# else use 'xset' to flash the
( xset led 3 && sleep $On && xset -led 3 ) # scroll-lock light on and off.
sleep `expr 10 - $On`
On=10 # Set on-time to 10 seconds.
#
# Raid status
grep blocks /proc/mdstat | grep _ >/dev/null 2>&1 && continue
#
# Filesystem capacity
df -x iso9660 |tr -d '%'|awk '{if (NR > 1) if ($5 > 90) exit 1}' || continue
#
# Swap usage
swapon -s | awk '{ if (NR > 1) { Size=Size+$3; Used=Used+$4 } }
END { if (Used*100/Size > 70 ) exit 1 }' || continue
#
On=1 # If there are no problems
done # reset on-time to 1 second.
If you are happy for 'ledblink' to run only when somebody is logged on with an Xwindows session, it's easy. If your machine has an 'xinitrc.d' directory, place the following script in it. Otherwise, place the uncommented line in the 'xinitrc' file.
#!/bin/sh # ledblink Place this file in: /usr/X11R6/lib/X11/xinit/xinitrc.d # and make it readable and executable for everyone. [ -x /usr/local/bin/ledblink ] && /usr/local/bin/ledblink &If you have the 'blinker' program, you can start 'ledblink' at boot time with the following script.
#!/bin/sh
# ledblink Start/stope the 'ledblink' system monitor program.
# Graham Jenkins, IBM GSA, July 2003.
#
# chkconfig: 2345 98 7
# description: Start/stops the 'ledblink' system monitor program.
case "$1" in
start) if [ -x /usr/local/bin/ledblink ] ; then
[ -s /var/run/ledblink.pid ] && exit 0
echo "Starting 'ledblink' system monitor program .."
/usr/local/bin/ledblink &
echo $! >/var/run/ledblink.pid
fi ;;
stop) if [ -n "`cat /var/run/ledblink.pid`" ] ; then
echo "Stopping 'ledblink' system monitor program .."
kill `cat /var/run/ledblink.pid`
rm /var/run/ledblink.pid
fi ;;
esac
![[picture]](../gx/2003/authors/Graham_Jenkins.jpg) Graham is a Unix Specialist at IBM Global Services, Australia. He lives
in Melbourne and has
built and managed many flavors of proprietary and open systems on several
hardware platforms.
Graham is a Unix Specialist at IBM Global Services, Australia. He lives
in Melbourne and has
built and managed many flavors of proprietary and open systems on several
hardware platforms.
|
...making Linux just a little more fun! |
By Avinoam Levkovich |
version 1.0
| The company I work for has
many old computers that are no longer suitable for the common application
today ( try Running Office XP/2k on a P-I 100MHZ with 32MB Ram, and you will
find out that this is not a pleasant experience ). We start looking for a
solution that will save the money of buying new computers or Brand
thin-clients. The goal was to use our old computer and still get good
performance . We find the Linux solution just great for my goals. we still use our old computer and the only investment we will have to make is buying the Windows 2K/2003 licenses and hardware . |
|
|
The solution is actually an integration of the following Sub systems : LTSP, rdesktop and wilisystem , fortunately those systems are integrating quite naturally as you will see . |
|
| LTSP ( http://www.ltsp.org ) : Is the backbone of all the system which provide the Linux terminal services for the diskless client. after installing LTSP it create the /opt/ltsp/i386 Directory. |
|
| this Directory will be the
root system of our diskless clients. when booting the client it will
get its kernel by tftp from LTSP and then it will mount /opt/ltsp/i386 as
its root directory.
So after your client finish its boot process you will be logged to your LTSP Server and your file system will be the /opt/ltsp/i386 Directory. and then the Wilisystem start Working. |
|
|
|
|
Rdesktop :
http://www.rdesktop.org/ Microsoft has developed a protocol called RDP which is used for the Terminal Server communication with the client. The rdesktop package is an application that opens RDP Session with a Windows Server and by doing it , the Linux station become a Windows Terminal Client. |
|
|
|
|
Wilisystem (
http://www.wilisystem.com/
) :
The Wilisystem is actually a patch for the LTSP server. what is does is make the connection to the Windows Terminal Server as easy as it can get. The Wilisystem uses the rdesktop package and finish the Diskless client boot process with the Windows login screen. by doing this it make the LTSP Session invisible to the user who feel as if he is plugged directly to the Windows Server . I must thank the wilisystem developers for a great job ! |
|
|
|
|
Rom-O-Matic : www.rom-o-matic.net This is where you get you boot image for you selected boot Device ( I used a floppy ). after specifying your Ethernet card model you can download your boot image. Great implementation for a great idea. |
|
|
|
|
please read the documentation from the Above web site's. when you read the documentation you will discover all the options and benefits that you can get from this system and how to tune it to your needs.
|
|
| what you need : | |
| 1. | Linux Server , I used P-III 800 with 256MB RAM , With Red Hat 9.0 . |
| 2. | Diskless Client, I used a P-I 133MHZ , 32MB RAM, Ati - Rage XL (mach64 Family) Display Adaptor, with the intel 100/pro Ethernet . |
| 3. | Windows 2K/2003 Server With Terminal Services installed, configured and Running . |
| I used a P-4 1.7MHZ with 256MB RAM. | |
| Create your diskless Client Environment: | |
| The Diskless Client will be called ws009. | |
| The Linux Server Side : | |
| 1. | Find your Client ( ws009 ) Display card Model and his Ethernet mac address and write them down, you will need them later. |
| 2. | Download and install the Following packages from http://www.ltsp.org : |
| ltsp_core-X.X-X.rpm ltsp_kerne-X.X-X.rpm ltsp_x_core-X.X-X.rpm ltsp_x_fonts-X.X-X.rpm |
|
| 3. | Install the rdesktop package from your RedHat CD or Download it form http://www.rdesktop.org/ . |
| 4. | Download the wilisystem patch from www.wilisystem.com , and install it . |
| 5. | Make sure that the packages for the Dhcp,Nfs,Tftp servers are installed. |
| 6. | Edit the file /opt/ltsp/install_scripts/CONFIG and change the settings to match your network Setting. |
| 7. | Run /opt/ltsp/templates/ltsp_initialize |
|
# cd /opt/ltsp/templates/ltsp_initialize # ./ltsp_initialize |
|
| 8. |
Copy /etc/dhcpd.conf.example to /etc/dhcpd.conf and check that all the network numbers match your network Configuration. |
| Check the Mac address of your client and update the client configuration section ( host ws009 ) in the dhcpd.conf file. | |
Here is my /etc/dhcpd.conf :
host ws009 { |
|
| 9. | Check /etc/exports. check that the IP numbers match your network Configuration. if everything is fine run : |
|
# exportfs -r # exportfs -a |
|
| 10. | Check that your client is properly listed in /etc/hosts. |
| if your client name is w009 and your domain is
my-domain.com you should add a line to your /etc/hosts file
like : 192.168.1.112 ws009.my-domain.com ws009 this name (ws009) should be the same as the client name ( host ws009) that you configured in your dhcp.conf |
|
| 12. | Check /opt/ltsp/i386/etc/lts.conf at the end of the file you should see the wilisystem configuration |
Here is my Wilisystem Config , I added my remarks for the configuration part: # Config part for the
http://www.wilisystem.com # the folowing line configure your mouse , check the Documentation page for more mouse type configuration : http://www.ltsp.org/documentation/
|
|
| 13. | Make sure that the tftp service is enabled in the xinetd directory. |
| run : # service dhcpd restart # service xinetd restart # service nfs restart |
|
| The verify that the tftp server is running. run
: netstat -anp | grep ":69 " you should get something like : udp 0 0 0.0.0.0:69 0.0.0.0:* 799/xinetd verify dhcp server by : netstat -anp | grep ":67 " you should get something like : udp 0 0 0.0.0.0:67 0.0.0.0:* 2086/dhcpd If dhcp is not working try restarting it . If tftp is not working then you have to enable tftp in /etc/xinetd.d/tftp and restart it. |
|
| 14. | The default runlevel is specified in /opt/ltsp/i386/etc/lts.conf is runlevel 5 BUT in the wilisystem section it override the default with its own Runlevel 7 ( if you take a look at /opt/ltsp/i386/etc/inittab you will see wilisystem Configuration for this runlevel.). |
| if you exerience
problems you should change it. try to load your client with one of the other
clients configuration that you have in
/opt/ltsp/i386/etc/lts.conf , ws001 is a good start . remember to change your
dhcp configuration and your hosts file to match your new host name. and
choose the runlevel 3 . this will only load the ltsp system without trying
to connect to the Windows Terminal Server.
then you will be able to debug the system. |
|
| The Diskless Client Side | |
| 1. | Get your initial client boot kernel from : http://rom-o-matic.net/ |
| To creat a boot floppy from the image you downloaded run : | |
| # cat eb-5.0.10-yournic.lzdsk > /dev/fd0 | |
| where "eb-5.0.10-yournic.lzdsk" is where you stored your downloaded ROM image. | |
| 2. | Reboot the client with the boot floppy that you created from the boot image. |
| After The boot process finished ,you should get the Windows logon screen :-) | |
|
|
|
| Problems ===================== |
|
| i experienced screen flickers when the X Server was trying to load and failes with message "no screens found " , it was because the system didnt recognized my display adaptor , which is "mach64" family , it was solved after I downloaded the proper Xfree 3.3 Drivers from the ltsp site. and I used the " XSERVER = XF86_Mach64 " in the lts.conf file. | |
![[BIO]](../gx/2002/note.png)
|
...making Linux just a little more fun! |
By Bhaskaran |
It is apparent that support for networking is inherent to the Linux kernel. One could also see Linux as one of the most 'safest and secure' Networking Operating system presently available in the market. Internally Linux kernel implements the TCP/IP protocol stack . It is possible to divide the networking code into parts - one which implements the actual protocols (the /usr/linux/net/ipv4 directory) and the other which implements device driver various network hardware.(/usr/src/linux/drivers/net ).
The kernel code for TCP/IP is written in such a way that it is very simple to "slide in" drivers for many kind of real (or virtual) communication channels without bothering too much about the functioning of the network and transport layer code. It just requires a module in a standard manner, connecting the card hardware to actual software interface. The hardware part consists of an Ethernet card in case of LAN or a modem in internet.
Now a days a lot of Networking cards are available in the market, one of them is RTL8139 PCI ethernet card. RTL8139 cards are plug and play kind of devices, connected to the cpu through PCI bus scheme. PCI stands for Peripheral Component Interconnect, it's a complete set of specifications defining how different parts of computer interact with others. PCI architecture was designed as a replacement to earlier ISA standards because of its promising features like speed of data transfer, independent nature, simplification in adding and removing a device etc.
Another important way is by manually detecting and configuring a network card, for which ifconfig command is used. A typical output of ifconfig command without any arguments is shown below (it could vary system to system depending upon the configuration).
eth0 Link encap:Ethernet HWaddr 00:80:48:12:FE:B2
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:10 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 b) TX bytes:600 (600.0 b)
Interrupt:11 Base address:0x7000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:4 errors:0 dropped:0 overruns:0 frame:0
TX packets:4 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:336 (336.0 b) TX bytes:336 (336.0 b)
It shows that I have a running interface for eth0 and lo, which corresponds to ethernet card and loopback interface respectively. The loopback is completely software based and used as an dummy interface to the network. The eth0 is the default name given to real hardware interface for realtek 8139 network card. The listing also tells about its hardware (HWaddr), internet (inet addr), Broadcast(Bcast), Mask (Mask) addresses with some other statistical information on data transfer that include Maximum data unit that can be transferred (MTU), no. of received (RX) packets, no. of transmitted packets (TX), collisions etc. The ifconfig command can also be used to bring up the interface if it is not detected at boot time. This could also be associated with an IP address as given below.
ifconfig eht0 192.9.200.1 upThis brings up the ethernet card to listen to an IP address 192.9.200.1, a class-C client. At the same time ifoconfig can also be used to bring down an activated interface. This is as given below.
ifconfig eth0 downThe same is applicable to loopback interface. That is these are quite possible.
ifconfig lo 192.9.200.1 up ifconfig lo down'ifconfig' supports plenty of options that may be discovered through reference to man pages.
Another command that needs reference is netstat, It prints out network connections, routing tables, interface statistics, masquerade connections, and multicast memberships. An exhaustive list of options may be found in man pages.
Kernel as usual provides concise but efficient data structures and functions to perform elegant programming, even understandable to a moderate programmer, and the interface provided is completely independent of higher protocol suit. For an quick overview of the kernel data structures, functions, the interactions between driver and upper layer of protocol stack, we first attempt to develop a hardware independent driver. Once we get a big picture we can dig into the real platform.
Whenever a module is loaded into kernel memory, it requests the resources needed for its functioning like I/O ports, IRQ etc. Similarly when a network driver registers itself; it inserts a data structure for each newly detected interface into a global list of network devices.
Each interface is defined by a struct net_device item. The declaration of device rtl8139 could done as follows
struct net_device rtl8139 = {init: rtl8139_init};
The struct net_device structure is defined in include file linux/net_device.h .The code above initializes only a single field 'init' that carries the initialization functions. Whenever we register a device the kernel calls this init function, which initializes the hardware and fills up struct net_device item. The struct net_device is huge and handles all the functions related to operations of the hardware. Let us look upon some revelent ones.
name : The first field that needs explanation is the 'name' field, which holds the name of the interface (the string identifying the interface). Obviously it is the string "rtl8139" in our case.
int (*open) (struct net_device *dev) : This method opens the interface whenever ifconfig activates it. The open method should register any system resource it needs.
int (*stop) (struct net_device *dev) : This method closes or stops the interface (like when brought down by ifconfig).
int (*hard_start_xmit) (struct sk_buff *skb, struct net_device *dev) : This method initiates the transmission through the device 'dev'. The data is contained in the socket buffer structure skb. The structure skb is defined later.
struct net_device * (*get_status) (struct net_device *dev): Whenever a application needs to get statistics for the interface, this method is called. This happens, for example, when ifconfig or netstat -i is run.
void *priv :The driver writer owns this pointer and can use it at will. The utility of this member will be persuaded at a later stage. There exist a lot more methods to be explained but before that let us look at some working code demonstration of a dummy driver built upon the discussion above. This code would make the interactions between these elements crystal clear.
Code Listing 1
#define MODULE
#define __KERNEL__
#include < linux/module.h >
#include < linux/config.h >
#include < linux/netdevice.h >
int rtl8139_open (struct net_device *dev)
{
printk("rtl8139_open called\n");
netif_start_queue (dev);
return 0;
}
int rtl8139_release (struct net_device *dev)
{
printk ("rtl8139_release called\n");
netif_stop_queue(dev);
return 0;
}
static int rtl8139_xmit (struct sk_buff *skb,
struct net_device *dev)
{
printk ("dummy xmit function called....\n");
dev_kfree_skb(skb);
return 0;
}
int rtl8139_init (struct net_device *dev)
{
dev->open = rtl8139_open;
dev->stop = rtl8139_release;
dev->hard_start_xmit = rtl8139_xmit;
printk ("8139 device initialized\n");
return 0;
}
struct net_device rtl8139 = {init: rtl8139_init};
int rtl8139_init_module (void)
{
int result;
strcpy (rtl8139.name, "rtl8139");
if ((result = register_netdev (&rtl8139))) {
printk ("rtl8139: Error %d initializing card rtl8139 card",result);
return result;
}
return 0;
}
void rtl8139_cleanup (void)
{
printk ("<0> Cleaning Up the Module\n");
unregister_netdev (&rtl8139);
return;
}
module_init (rtl8139_init_module);
module_exit (rtl8139_cleanup);
This typical module defines its entry point at rtl8139_init_module
function. The method defines a net_device, names it to be "rtl8139" and
register this device into kernel. Another important function rtl8139_init inserts the dummy functions rtl8139_open, rtl8139_stop, rtl8139_xmit to net_device structure. Although dummy functions, they perform a little task, whenever the rtl8139 interface is activated. When the rtl8139_open is called - then this routine announces the readiness of the driver to accept data by calling netif_start_queue. Similarly it gets stopped by calling netif_stop_queue.
Let us compile the above program and play with it. A command line invocation of 'cc' like below is sufficient to compile our file rtl8139.c
[root@localhost modules]# cc -I/usr/src/linux-2.4/include/ -Wall -c rtl8139.c
Let us check our dummy network driver. The following output was obtained on my system. We can use lsmod for checking the existing loaded modules. A output of lsmod is also shown.
(NB: You should be a super user in order to insert or delete a module.)
[root@localhost modules]# insmod rtl8139.o
Warning: loading test.o will taint the kernel: no license
See http://www.tux.org/lkml/#export-tainted for information about tainted modules
Module test loaded, with warnings
[root@localhost modules]# lsmod
Module Size Used by Tainted: P
rtl8139 2336 0 (unused)
mousedev 5492 1 (autoclean)
input 5856 0 (autoclean) [mousedev]
i810 67300 6
agpgart 47776 7 (autoclean)
autofs 13268 0 (autoclean) (unused)
[root@localhost modules]# ifconfig rtl8139 192.9.200.1 up
[root@localhost modules]# ifconfig
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:4 errors:0 dropped:0 overruns:0 frame:0
TX packets:4 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:336 (336.0 b) TX bytes:336 (336.0 b)
rtl8139 Link encap:AMPR NET/ROM HWaddr
inet addr:192.9.200.1 Mask:255.255.255.0
UP RUNNING MTU:0 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:10 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 b) TX bytes:600 (600.0 b)
Now You have been acquainted with writing a dummy driver, Let us move on to
a real driver interface for rtl8139.
Though Network interface has been built up, but still it is not possible for us to probe and initialize the card. This is only possible until we check for a PCI interface and a PCI device available. Thus it becomes necessary that we have a close look upon the PCI and PCI functions available.
As I have described earlier that the PCI hardware is a complete protocol that determines the way each components interaction with the other. Each PCI device is identified by a bus number, a device number and a function number. The PCI specification permits a system to hold upon 256 buses, with each buses having a capacity to hold 32 multiboard devices.
The PC firmware initializes PCI hardware at system boot, mapping each devices I/O region to a different address, which is accessible from PCI configuration space, which consist of 256 bytes for each device. Three of the PCI registers identify a device: vendorID, deviceID, class. Sometimes Subsystem vendorID and Subsystem deviceID are also used. Let us see them in detail.
A complete list of PCI devices on ones linux box could be seen through command lspci.
Based on the above information we can perform the detection of the rtl8139 could done in the rtl8139_init function itself, a modified version will look like
Code Listing 2
#include < linux/pci.h >
static int rtl8139_probe (struct net_device *dev, struct pci_dev *pdev)
{
int ret;
unsigned char pci_rev;
if (! pci_present ()) {
printk ("No pci device present\n");
return -ENODEV;
}
else printk ("<0> pci device were found\n");
pdev = pci_find_device (PCI_VENDOR_ID_REALTEK,
PCI_DEVICE_ID_REALTEK_8139, pdev);
if (pdev) printk ("probed for rtl 8139 \n");
else printk ("Rtl8193 card not present\n");
pci_read_config_byte (pdev, PCI_REVISION_ID, &pci_rev);
if (ret = pci_enable_device (pdev)) {
printk ("Error enabling the device\n");
return ret;
}
if (pdev->irq < 2) {
printk ("Invalid irq number\n");
ret = -EIO;
}
else {
printk ("Irq Obtained is %d",pdev->irq);
dev->irq = pdev->irq;
}
return 0;
}
int rtl8139_init (struct net_device *dev)
{
int ret;
struct pci_dev *pdev = NULL;
if ((ret = rtl8139_probe (dev, pdev)) != 0)
return ret;
dev->open = rtl8139_open;
dev->stop = rtl8139_release;
dev->hard_start_xmit = rtl8139_xmit;
printk ("My device initialized\n");
return 0;
}
As you can see a probe funtion is called through rtl8139_init function. A detailed analysis of the probe functions shows that it has been passed pointers of kind struct net_device and struct pci_dev. The struct pci_dev holds the pci interface and other holds the network interface respectively, which has been mentioned earlier.
The function pci_present checks for a valid pci support available. It returns a value '0' on Success. Thereafter a probe of RTL8139 is initiated through the pci_find_device function. It accepts the vendor_ID, device_ID and the 'pdev' structure as argument. On an error-free return i.e. when RTL8139 is present, it sends the pdev structure filled. The constants PCI_VENDOR_ID_REALTEK, PCI_DEVICE_ID_REALTEK_8139 defines the vendorID and device_ID of the realtek card. These are defined in linux/pci.h.
pci_read_config_byte/word/dword are functions read byte/word/dword memory locations from the configuration space respectively. A call to pci_enable function to enable pci device for rtl8139, which also helps in registering its interrupt number to the interface. Hence if everything goes safe and error-free, your rtl_8139 has been detected and assigned an interrupt number.
In the next section we would see how to detect the hardware address of rtl8139 and start communication.
![[BIO]](../gx/2002/note.png) Author has just completed B.Tech from Govt. Engg. College Thrissur.
Author has just completed B.Tech from Govt. Engg. College Thrissur.
|
...making Linux just a little more fun! |
By Hiran Ramankutty |
The next version of the calculator to be described below is substantially much more complex with major changes in the inclusion of if-then-else and while constructs. In addition a syntax tree is constructed during parsing. We can traverse or walk down the tree to get the output. Designing of the tree walk routine can be done in two ways:
To make things more concrete, here is a sample program.
x = 0;
while(x < 3) {
print x;
x = x + 1;
}
The output of the interpretive version will be:
1 2 3
while that of the compiler version will be:
push 0 push x LC0: push x push 3 complt jz LC1 push x print push x push 1 add pop x jmp LC0 LC1: ret
The include file contains declarations for the syntax tree and symbol table. The symbol table, sym allows for single character variable names. A node in the syntax tree may hold a constant, an identifier or an internal node with an operator. All three variants are encapsulated in a union nodetype and the structure we have can be determined by nodetype.type.
The lex input file contains patterns for VARIABLE and INTEGER tokens. In addition, tokens are identified for two-character operators such as EQ and NE. Single character operators are simply returned as themselves.
The yacc input file defines YYSTYPE, the type of yylval, as
%union {
int ivalue; /* integer value */
char sIndex; /* symbol table index */
nodeType *nPtr; /* node pointer */
};
This causes the following to be generated in y.tab.h:
typedef union {
int iValue; /* integer value;
char sIndex; /* symbol table index */
nodeType *nPtr; /* node pointer */
}YYSTYPE;
extern YYSTYPE yylval;
Constants, variables and nodes can be represented by yylval in the parser's value stack. Notice the type definitions
%token <iValue> INTEGER %token <nPtr> expr
This binds expr to nPtr, and INTEGER to iValue in the YYSTYPE union. This is essential so that yacc can generate the correct code. For example, the rule
expr: INTEGER { $$ = con($1); }
should generate the following code.
yylval.nPtr = con(yyvsp[0].iValue);
Note that yyvsp is the value stack pointer and yyvsp[0] addresses the top of the value stack, or the value associated with INTEGER.
The unary minus operator is given higher priority than binary operators as follows:
%left GE LE EQ NE '<' '>' %left '+' '-' %left '*' '/' %nonassoc UMINUS
The %nonassoc indicates no associativity is implied. It is frequently used in conjunction with %prec to specify precedence as a rule.
The bottom-up technique is used to construct the syntax tree. Leaf nodes are allocated as integers and variables are reduced. When operators are encountered, a node is allocated and pointers to previously allocated nodes are entered as operands. As statements are reduced, ex is called to do a depth-first walk of the syntax tree. Since the tree was constructed bottom-up, a depth first walk visits nodes in the order that they were originally allocated. This results in operators being applied in the order that they were encountered during parsing.
typedef enum { typeCon, typeId, typeOpr } nodeEnum;
/* constants */
typedef struct {
nodeEnum type; /* type of node */
int value; /* value of constant */
} conNodeType;
/* identifiers */
typedef struct {
nodeEnum type; /* type of node */
int i; /* subscript to ident array */
} idNodeType;
/* operators */
typedef struct {
nodeEnum type; /* type of node */
int oper; /* operator */
int nops; /* number of operands */
union nodeTypeTag *op[1]; /* operands (expandable) */
} oprNodeType;
typedef union nodeTypeTag {
nodeEnum type; /* type of node */
conNodeType con; /* constants */
idNodeType id; /* identifiers */
oprNodeType opr; /* operators */
} nodeType;
extern int sym[26];
%{
#include <stdlib.h>
#include "calc3.h"
#include "y.tab.h"
void yyerror(char *);
%}
%%
[a-z] {
yylval.sIndex = *yytext - 'a';
return VARIABLE;
}
[0-9]+ {
yylval.iValue = atoi(yytext);
return INTEGER;
}
[-()<>=+*/;{}.] {
return *yytext;
}
">=" return GE;
"<=" return LE;
"==" return EQ;
"!=" return NE;
"while" return WHILE;
"if" return IF;
"else" return ELSE;
"print" return PRINT;
[ \t\n]+ ; /* ignore whitespace */
. yyerror("Unknown character");
%%
int yywrap(void) {
return 1;
}
%{
#include <stdio.h>
#include <stdlib.h>
#include <stdarg.h>
#include "calc3.h"
/* prototypes */
nodeType *opr(int oper, int nops, ...);
nodeType *id(int i);
nodeType *con(int value);
void freeNode(nodeType *p);
int ex(nodeType *p);
int yylex(void);
void yyerror(char *s);
int sym[26]; /* symbol table */
%}
%union {
int iValue; /* integer value */
char sIndex; /* symbol table index */
nodeType *nPtr; /* node pointer */
};
%token <iValue> INTEGER
%token <sIndex> VARIABLE
%token WHILE IF PRINT
%nonassoc IFX
%nonassoc ELSE
%left GE LE EQ NE '>' '<'
%left '+' '-'
%left '*' '/'
%nonassoc UMINUS
%type <nPtr> stmt expr stmt_list
%%
program:
function { exit(0); }
;
function:
function stmt { ex($2); freeNode($2); }
| /* NULL */
;
stmt:
';' { $$ = opr(';', 2, NULL, NULL); }
| expr ';' { $$ = $1; }
| PRINT expr ';' { $$ = opr(PRINT, 1, $2); }
| VARIABLE '=' expr ';' { $$ = opr('=', 2, id($1), $3); }
| WHILE '(' expr ')' stmt
{ $$ = opr(WHILE, 2, $3, $5); }
| IF '(' expr ')' stmt %prec IFX
{ $$ = opr(IF, 2, $3, $5); }
| IF '(' expr ')' stmt ELSE stmt
{ $$ = opr(IF, 3, $3, $5, $7); }
| '{' stmt_list '}' { $$ = $2; }
;
stmt_list:
stmt { $$ = $1; }
| stmt_list stmt { $$ = opr(';', 2, $1, $2); }
;
expr:
INTEGER { $$ = con($1); }
| VARIABLE { $$ = id($1); }
| '-' expr %prec UMINUS { $$ = opr(UMINUS, 1, $2); }
| expr '+' expr { $$ = opr('+', 2, $1, $3); }
| expr '-' expr { $$ = opr('-', 2, $1, $3); }
| expr '*' expr { $$ = opr('*', 2, $1, $3); }
| expr '/' expr { $$ = opr('/', 2, $1, $3); }
| expr '<' expr { $$ = opr('<', 2, $1, $3); }
| expr '>' expr { $$ = opr('>', 2, $1, $3); }
| expr GE expr { $$ = opr(GE, 2, $1, $3); }
| expr LE expr { $$ = opr(LE, 2, $1, $3); }
| expr NE expr { $$ = opr(NE, 2, $1, $3); }
| expr EQ expr { $$ = opr(EQ, 2, $1, $3); }
| '(' expr ')' { $$ = $2; }
;
%%
nodeType *con(int value) {
nodeType *p;
/* allocate node */
if ((p = malloc(sizeof(conNodeType))) == NULL)
yyerror("out of memory");
/* copy information */
p->type = typeCon;
p->con.value = value;
return p;
}
nodeType *id(int i) {
nodeType *p;
/* allocate node */
if ((p = malloc(sizeof(idNodeType))) == NULL)
yyerror("out of memory");
/* copy information */
p->type = typeId;
p->id.i = i;
return p;
}
nodeType *opr(int oper, int nops, ...) {
va_list ap;
nodeType *p;
size_t size;
int i;
/* allocate node */
size = sizeof(oprNodeType) + (nops - 1) * sizeof(nodeType*);
if ((p = malloc(size)) == NULL)
yyerror("out of memory");
/* copy information */
p->type = typeOpr;
p->opr.oper = oper;
p->opr.nops = nops;
va_start(ap, nops);
for (i = 0; i < nops; i++)
p->opr.op[i] = va_arg(ap, nodeType*);
va_end(ap);
return p;
}
void freeNode(nodeType *p) {
int i;
if (!p) return;
if (p->type == typeOpr) {
for (i = 0; i < p->opr.nops; i++)
freeNode(p->opr.op[i]);
}
free (p);
}
void yyerror(char *s) {
fprintf(stdout, "%s\n", s);
}
int main(void) {
yyparse();
return 0;
}
#include <stdio.h>
#include "calc3.h"
#include "y.tab.h"
int ex(nodeType *p) {
if (!p) return 0;
switch(p->type) {
case typeCon: return p->con.value;
case typeId: return sym[p->id.i];
case typeOpr:
switch(p->opr.oper) {
case WHILE: while(ex(p->opr.op[0]))
ex(p->opr.op[1]);
return 0;
case IF: if (ex(p->opr.op[0]))
ex(p->opr.op[1]);
else if (p->opr.nops > 2)
ex(p->opr.op[2]);
return 0;
case PRINT: printf("%d\n", ex(p->opr.op[0]));
return 0;
case ';': ex(p->opr.op[0]);
return ex(p->opr.op[1]);
case '=': return sym[p->opr.op[0]->id.i] =
ex(p->opr.op[1]);
case UMINUS: return -ex(p->opr.op[0]);
case '+': return ex(p->opr.op[0]) + ex(p->opr.op[1]);
case '-': return ex(p->opr.op[0]) - ex(p->opr.op[1]);
case '*': return ex(p->opr.op[0]) * ex(p->opr.op[1]);
case '/': return ex(p->opr.op[0]) / ex(p->opr.op[1]);
case '<': return ex(p->opr.op[0]) < ex(p->opr.op[1]);
case '>': return ex(p->opr.op[0]) > ex(p->opr.op[1]);
case GE: return ex(p->opr.op[0]) >= ex(p->opr.op[1]);
case LE: return ex(p->opr.op[0]) <= ex(p->opr.op[1]);
case NE: return ex(p->opr.op[0]) != ex(p->opr.op[1]);
case EQ: return ex(p->opr.op[0]) == ex(p->opr.op[1]);
}
}
}
#include <stdio.h>
#include "calc3.h"
#include "y.tab.h"
static int lbl;
int ex(nodeType *p) {
int lbl1, lbl2;
if (!p) return 0;
switch(p->type) {
case typeCon:
printf("\tpush\t%d\n", p->con.value);
break;
case typeId:
printf("\tpush\t%c\n", p->id.i + 'a');
break;
case typeOpr:
switch(p->opr.oper) {
case WHILE:
printf("L%03d:\n", lbl1 = lbl++);
ex(p->opr.op[0]);
printf("\tjz\tL%03d\n", lbl2 = lbl++);
ex(p->opr.op[1]);
printf("\tjmp\tL%03d\n", lbl1);
printf("L%03d:\n", lbl2);
break;
case IF:
ex(p->opr.op[0]);
if (p->opr.nops > 2) {
/* if else */
printf("\tjz\tL%03d\n", lbl1 = lbl++);
ex(p->opr.op[1]);
printf("\tjmp\tL%03d\n", lbl2 = lbl++);
printf("L%03d:\n", lbl1);
ex(p->opr.op[2]);
printf("L%03d:\n", lbl2);
} else {
/* if */
printf("\tjz\tL%03d\n", lbl1 = lbl++);
ex(p->opr.op[1]);
printf("L%03d:\n", lbl1);
}
break;
case PRINT:
ex(p->opr.op[0]);
printf("\tprint\n");
break;
case '=':
ex(p->opr.op[1]);
printf("\tpop\t%c\n", p->opr.op[0]->id.i + 'a');
break;
case UMINUS:
ex(p->opr.op[0]);
printf("\tneg\n");
break;
default:
ex(p->opr.op[0]);
ex(p->opr.op[1]);
switch(p->opr.oper) {
case '+': printf("\tadd\n"); break;
case '-': printf("\tsub\n"); break;
case '*': printf("\tmul\n"); break;
case '/': printf("\tdiv\n"); break;
case '<': printf("\tcompLT\n"); break;
case '>': printf("\tcompGT\n"); break;
case GE: printf("\tcompGE\n"); break;
case LE: printf("\tcompLE\n"); break;
case NE: printf("\tcompNE\n"); break;
case EQ: printf("\tcompEQ\n"); break;
}
}
}
}
7. If-Else Ambiguity
The shift-reduce conflict (as explained in Part 1) that frequently occurs
involves the if-else construct. Assume we have the following rules:
stmt:
IF expr stmt
| IF expr stmt ELSE stmt
...
and the following state:
IF expr stmt IF expr stmt . ELSE stmt
During parsing what do we do when we come across ELSE.Do we shift
the ELSE, or reduce the IF expr stmt at the top of the stack.
If we shift, then we have
IF expr stmt IF expr stmt . ELSE stmt
IF expr stmt IF expr stmt ELSE . stmt
IF expr stmt IF expr stmt ELSE stmt .
IF expr stmt stmt .
where the second ELSE is paired with the second IF. If we
reduce, we have
IF expr stmt IF expr stmt . ELSE stmt
IF expr stmt stmt . ELSE stmt
IF expr stmt . ELSE stmt
IF expr stmt ELSE . stmt
IF expr stmt ELSE stmt .
where the ELSE is paired with the first IF. Modern
programming languages pair an ELSE with the most recent unpaired
IF, and so the former behaviour is expected. This works well with
yacc. The default action of shifting is taken whenever a shift-reduce
conflict arises. Bur along with it, yacc issues a warning message. To
remove the message, give IF-ELSE a higher precedence than the simple
IF statement:
%nonassoc IFX
%nonassoc ELSE
stmt:
IF expr stmt %prec IFX
| IF expr stmt ELSE stmt
8. Conclusion
The conflicts resolved by precedence are not counted in the number of
shift/reduce and reduce/reduce conflicts reported by Yacc. This means that
mistakes in the specification of precedences may disguise errors in the
input grammar; it is a good idea to be sparing with precedences, and use
them in an essentially ``cookbook'' fashion, until some experience has been
gained. The y.output file is very useful in deciding whether the parser is
actually doing what was intended.
Yacc usually generates warnings. But errors may also arise. A message like
"syntax error" would leave you wandering where the error occurred and
what the error is. Error handling is much more difficult and I am not
dealing with it right now.
![[BIO]](../gx/2002/note.png) I have just given my final year B.Tech examinations in Computer Science and
Engineering and a native of Kerala, India.
I have just given my final year B.Tech examinations in Computer Science and
Engineering and a native of Kerala, India.
Copyright © 2003, Hiran Ramankutty.
Copying license http://www.linuxgazette.com/copying.html
Published in Issue 93 of Linux Gazette, August 2003
|
...making Linux just a little more fun! |
By Jeff Tinsler |
Posting of articles and making sure that the issue is published is now the SSC webmaster's job. As we progress to a total site makeover, you'll notice other minor changes such as the email addresses where authors submit articles, The Answer Gang, and others. The goal is to encourage more reader community participation both in article submissions and reader feedback forums. Ultimately, we hope to implement a CMS making participation easy and available for readers, authors, and me, the webmaster.
As we progress through the changes mentioned and reach what we believe to be our completed effort, we'll endeavor to create a forum for your input and suggestions. After all, if Linux Gazette isn't working for you, we'll want to know.
I hope you continue to enjoy not only this issue, but past and future Linux Gazette issues. Please come back often to see how we're doing.
SSC Webmaster
![[BIO]](../gx/2002/note.png) Webmaster for Linux Gazette and other SSC sites. Currently residing in
Costa Rica. Pura Vida!
Webmaster for Linux Gazette and other SSC sites. Currently residing in
Costa Rica. Pura Vida!